Overview
Contain attacks in seconds
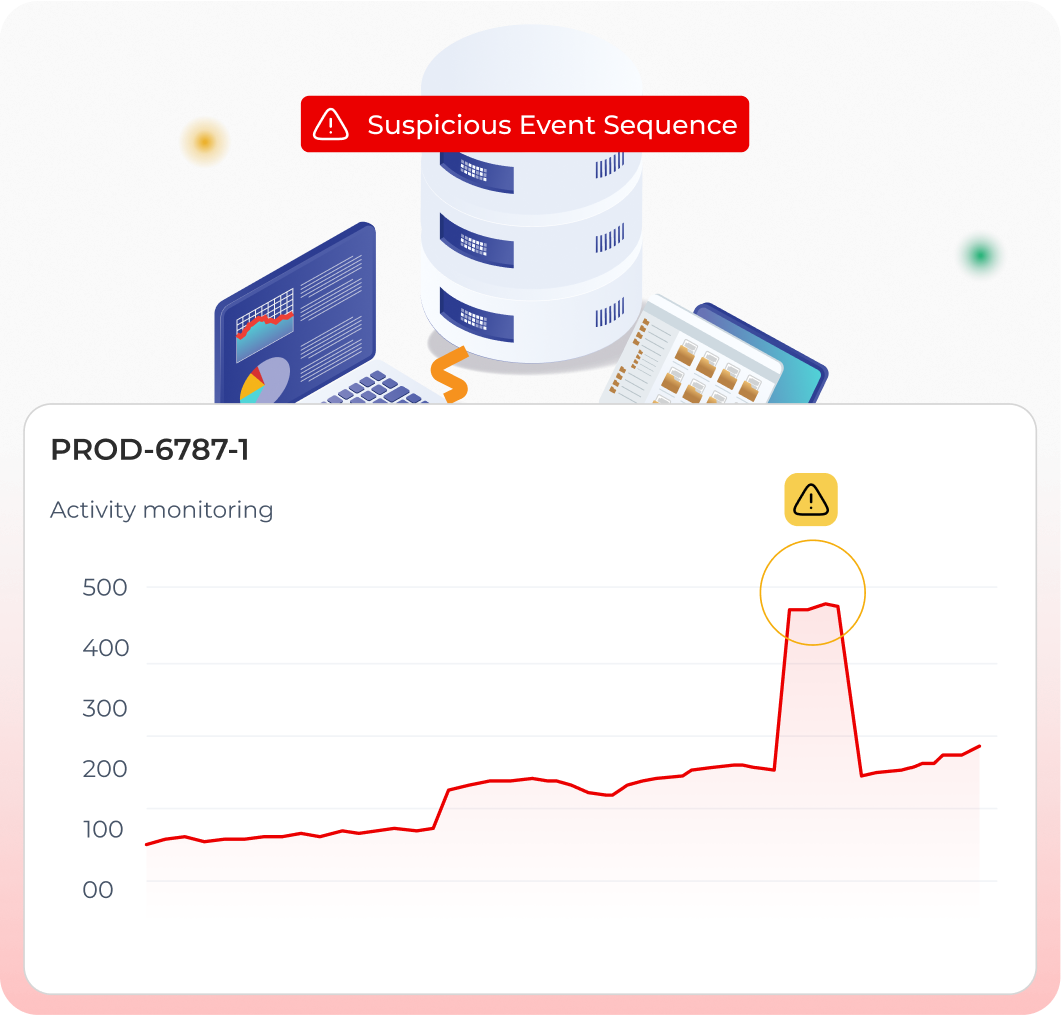
Legacy alerts arrive late and lack context. Lightbeam learns each user’s normal file activity, flags ransomware‑style spikes, then revokes access or isolates accounts instantly without agents.
The Lightbeam Advantage
-
Behavior‑aware detection across files and shares
Learn per‑user baselines; spot write, delete, and encryption bursts in minutes.
-
Identity‑centric blast‑radius clarity
See whose data is at risk and act with precision to prevent exfiltration of customer PII.
-
One‑click or automated containment
Suspend sessions, revoke access, or quarantine accounts directly in‑console.
-
Audit‑ready incident reporting
Exportable timeline of behaviors and actions for CISOs, auditors, and regulators.
Traditional Industry Approach
-
Periodic scans and signature rules
Miss fast encryption waves and insider deletions; alerts lag real‑time risk.
-
Siloed tools without identity context
Analysts lack clarity on what and whose data, slowing triage and inflating downtime.
-
Manual scripts for containment
Custom playbooks delay action while ransomware spreads across shares.
-
After‑the‑fact reporting
Forensics require stitching logs after impact without a provable kill chain.
Identity‑centric ransomware defense that acts in real time
Detect velocity spikes, tie them to people and data, and contain the blast radius
Lightbeam profiles reads, writes, deletes, and encrypts per identity across SharePoint, SMB, and cloud stores. When behavior veers from baseline, like a five‑fold write surge, the platform flags it with sensitivity and entitlement context, then suspends sessions or revokes access in one click, preserving an immutable audit trail.
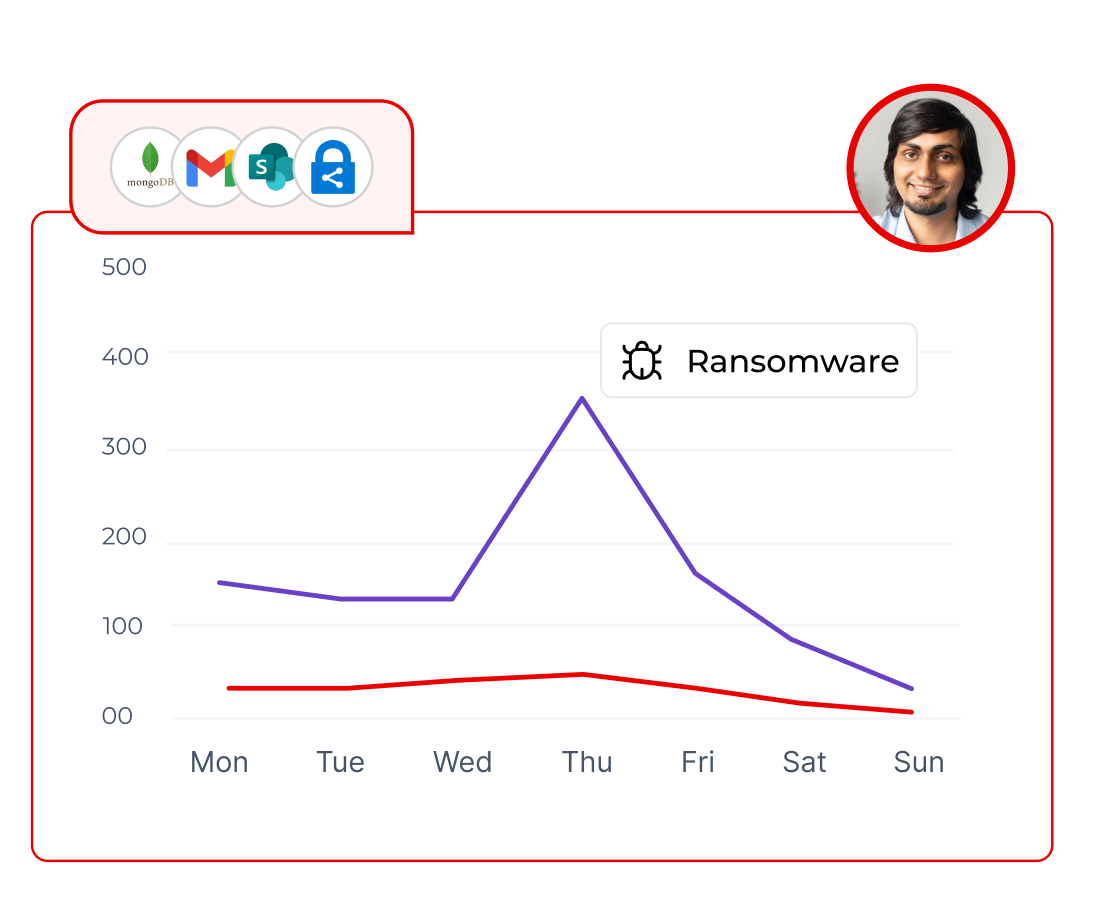
From anomaly to outcome: automate containment and prove resilience
UEBA signals flow into Access Governance playbooks so containment is instant: quarantine accounts, revoke open links, or snapshot folders without scripts. Executive‑ready incident reports stitch together behavior timelines, actions, and affected identities, demonstrating control to auditors and leadership.
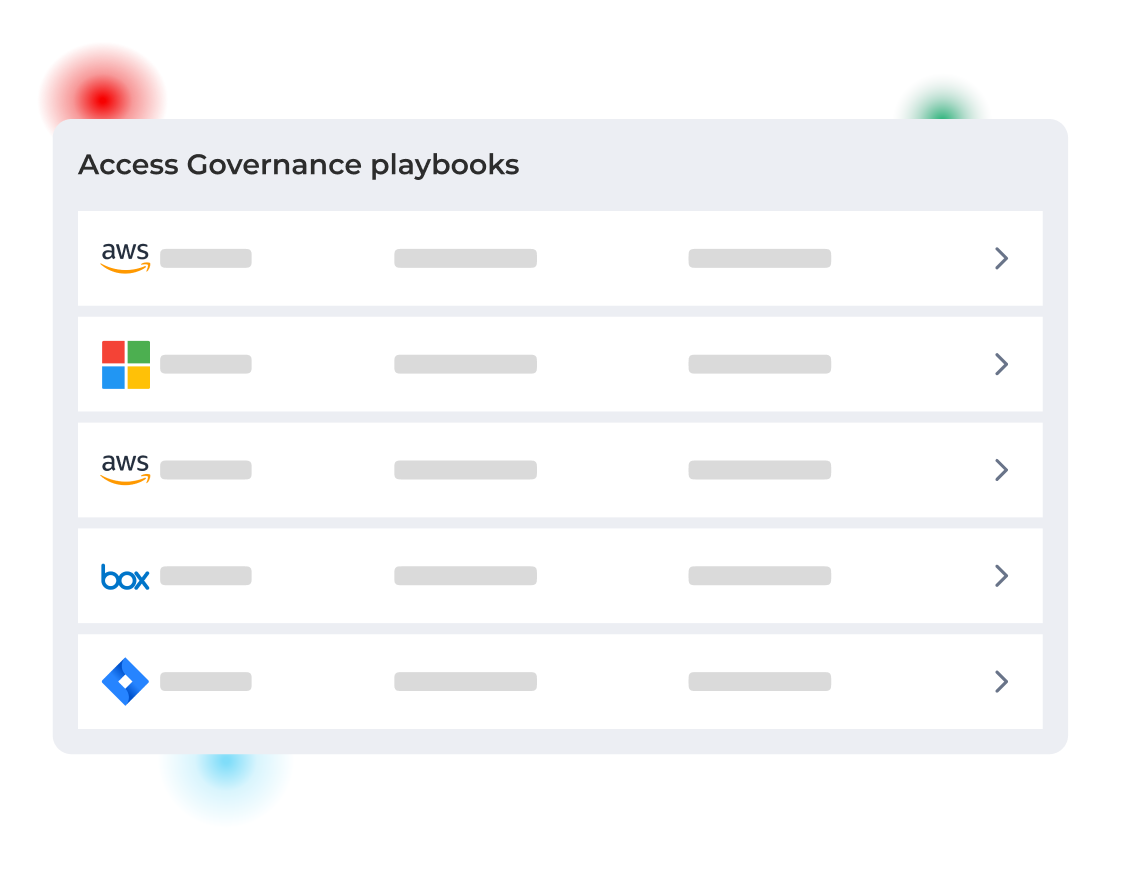
Cut alert noise, contain threats in seconds, and keep proof at your fingertips
Real‑time detection
Per‑user baselines flag ransomware‑style surges across writes, deletes, and encrypts, before sensitive data is exfiltrated.
Identity context
Know whose data is exposed and which accounts are compromised to prioritize the fastest, highest‑impact fixes.
One‑click containment
Suspend sessions, revoke access, or quarantine identities directly from the alert, with no scripts or extra consoles.
Audit‑ready reports
Timeline of behavior, actions, and outcomes creates provable resilience for CISOs, auditors, and regulators.
Cloud & On-Prem coverage
Protect SharePoint, OneDrive, Google Drive, Azure File Shares, and SMB with consistent policy enforcement.
What customers say
FAQs
Frequently Asked Questions
How does Lightbeam detect ransomware quickly without creating more alert noise?
The platform learns each identity’s normal cadence across reads, writes, deletes, and encrypts. Velocity spikes or unusual access to sensitive folders trigger alerts enriched with sensitivity and data context, so analysts see impact and can auto‑contain in seconds.
Read About UEBACan Lightbeam actually stop an active ransomware attack automatically?
Yes. Policy playbooks can suspend live sessions, revoke permissions, or quarantine compromised identities the moment thresholds are exceeded. Actions happen in the same console and are fully logged, preserving a defensible audit trail for post‑incident reporting.
Explore Automated RemediationHow is this different from traditional DLP or signature‑based tools we already use?
Traditional tools rely on periodic scans and static rules, which miss insider‑style surges. Lightbeam ties behavior to identity and access rights, then acts immediately with no scripts or extra consoles, reducing dwell time and delivering executive‑ready incident reports by default.
Explore Data ClassificationBrowse Key Resources
News
LightBeam Locks Down Copilot as New Front in Ransomware and Insider Risk Emerges
New release introduces AI Security and governance for Microsoft Copilot, behavioral containment, and UEBA to...