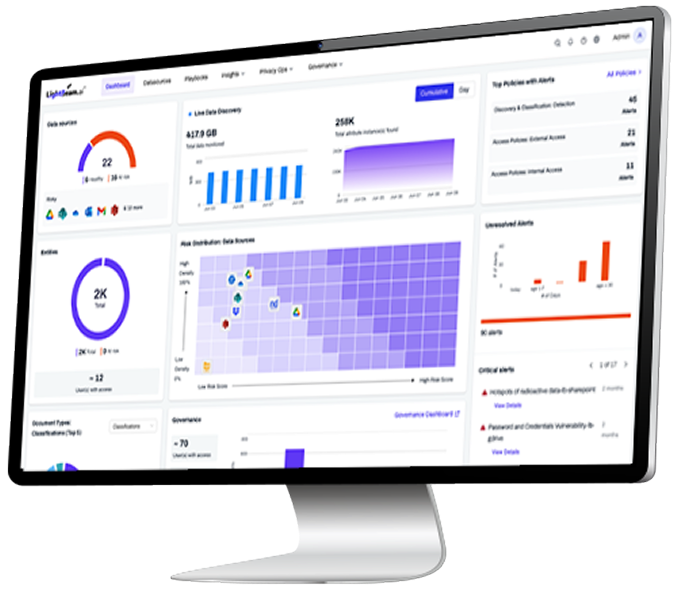
Untracked Access and Fast Attacks Put Data at Risk
Hidden Risk Everywhere
Shadow data, open shares, and forgotten backups let attackers in to steal at scale.
Ransomware Moves Fast
High-velocity encryption spreads in minutes, while alerts without context arrive too late.
Victim Trust Evaporates
Lost data means lost customers. Reputation damage lingers long after the breach response.

Reduce Breach Surface and Contain Ransomware Instantly
90%
Less exposed data
Cut risk by reducing open, overshared, and overretained files with sensitive data.
75%
Faster ransomware containment
Detect encryption surges, isolate compromised accounts, and contain threats in seconds.
95%
Breach cost avoided
Limit the blast radius of incidents and determine exactly what data and whose data was compromised.

“If a data breach occurred, it could have been a $100,000 issue. Now, with the Lightbeam platform, the cost of potential breaches becomes zero.”
Chris O’Leary
COO, Infinite Investment Systems
Automate Away Breach & Ransomware Risk
Instant Data Clarity
LightBeam lights up every sensitive data attribute, owner, and permission so security teams can spot exposures or ransomware blast radius instantly—without stale spreadsheets.
Explore Data Identity GraphSelf-Healing Access
Set guardrails once, then let automation revoke risky shares, stop mass encryption, and lock down accounts before breaches spread.
Explore Access GovernanceSingle Source of Truth
Converge DSPM, ransomware defense, and access governance in one console, eliminating silos and delivering executive-ready reports.
Explore Our PlatformRansomware Protection
UEBA baselines detect encryption or deletion bursts. Analysts can suspend sessions, revoke access, or quarantine accounts in one click.
See How Lightbeam Stops Ransomware



Map, Monitor, and Contain Threats in Seconds
LightBeam discovers sensitive data, maps it to real identities, monitors risky access, and automatically remediates exposures. Ransomware-style surges are detected in real time and contained instantly.
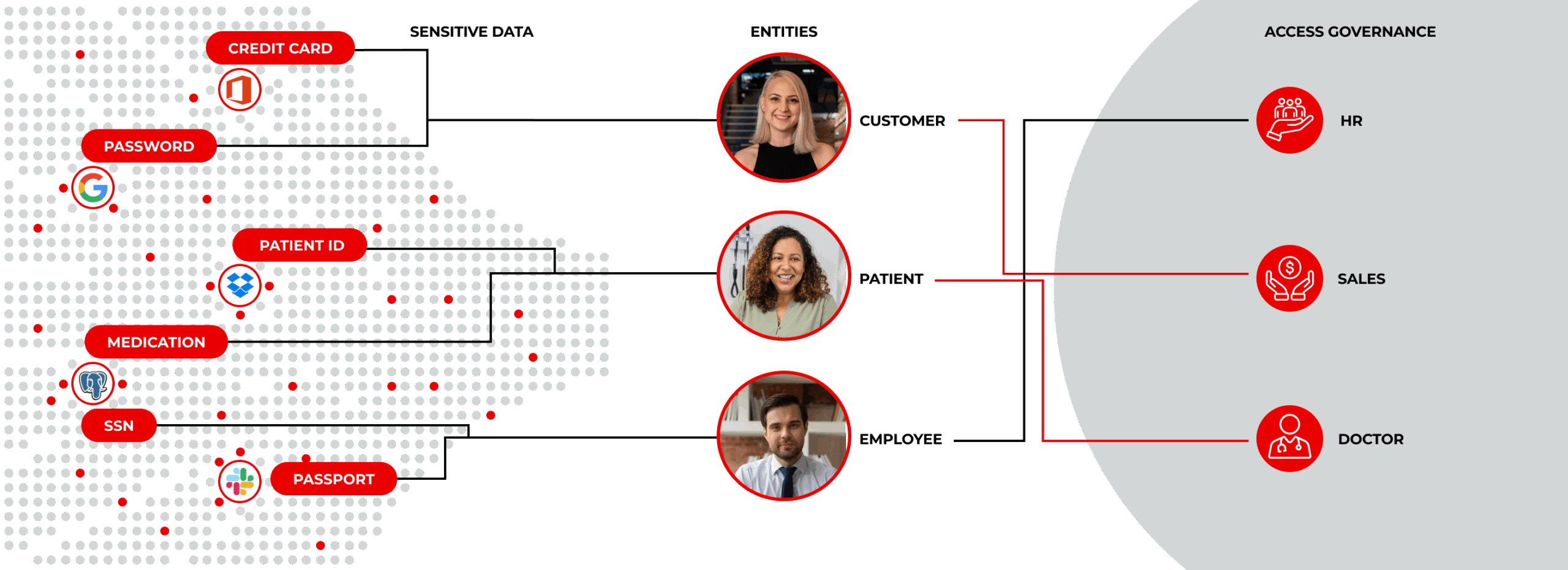
Extend protection across these related use cases

Data Security Posture Management (DSPM)
Discover and classify structured and unstructured data, surface risk, and reduce exposure at scale.
Learn More
Data Access Governance (DAG)
Enforce least privilege by ensuring only the right people access the right data, with full context.
Learn More
Ransomware Protection
Lightbeam detects rapid encryption or deletion, then auto-contains threats by revoking access, suspending sessions, and showing who, what, and where in one click.
Learn More
User and Entity Behavior Analysis
Lightbeam detects insider risk by baselining user behavior on sensitive data, then flags and remediates threats, showing who’s at risk, what moved, and why.
Learn MoreCustomers who love their results
Quick Answers
Frequently Asked Questions
How does Lightbeam detect a breach faster than traditional DLP?
Unlike DLP tools that look only at content patterns, the Lightbeam Data Identity Graph maps every sensitive element to its owner and typical access context. When an unusual movement or sharing event occurs, the platform raises an alert within minutes and can trigger automated remediation workflows. This contextual approach spots breaches early while reducing false positives.
Out PlatformCan we deploy the platform on-premises to keep data and metadata inside our own walls?
Yes. Lightbeam supports SaaS, private cloud, and fully on-premises deployments. With private cloud and on-premises deployments, your data never leaves your control.
Explore Our PlatformDoes Risk Scoring automatically revoke access when a file is risky?
Risk Scoring surfaces risk based on the content’s sensitivity and customizable weighting you define. It does not directly revoke access. Security teams can, however, build policies that act on high-risk scores, such as alerting, labeling, or revoking permissions, using the playbooks engine in the Lightbeam platform.
Dive into Risk Scoring