Top 10 DSPM (Data Security Posture Management) Best Practices for 2025
Henna
Table of Contents
- Why DSPM Matters in 2025
- 1. Continuous Data Discovery & Classification
- 2. Implement Identity-Centric Security
- 3. Monitor and Secure Shadow Data
- 4. Automate Risk-Based Access Control
- 5. Maintain Real-Time Compliance Monitoring
- 6. Integrate DSPM with DLP
- 7. Enforce Encryption & Data Masking
- 8. Continuously Assess Third-Party Risk
- 9. Automate Threat Detection & Response
- 10. Use Risk Scoring to Prioritize Remediation
- 11. Leverage AI and ML for Scalable DSPM
- Gartner-Recommended Practices for DSPM
- Future Trends in DSPM
- Conclusion
- FAQ Section (Snippet-Ready)
Why DSPM Matters in 2025
As data security threats become increasingly sophisticated, organizations must evolve beyond traditional controls and adopt smarter automated strategies. Data Security Posture Management (DSPM) plays a critical role in modern cybersecurity by offering visibility, control, and remediation across structured and unstructured data environments. To learn more about the basics of DSPM, read our blog “What is DSPM? And what can it do for you?
This guide outlines 10 DSPM best practices for 2025, enriched with Gartner guidance and powered by LightBeam’s identity-centric platform.

1. Continuous Data Discovery & Classification
Data security starts with visibility. You can’t protect what you can’t find. Organizations must continuously scan for and classify sensitive data across on-prem, SaaS, and multi-cloud environments.
How LightBeam Helps: LightBeam automatically discovers files, tables, emails, or tickets that contain sensitive data—no matter where they live. Then it classifies each data element using AI, and the context of the content, location, and how it’s used. But we don’t stop there: we also link each piece of data to a real person—a customer, employee, patient, or shopper—so you know whose data it is and how it’s being handled.
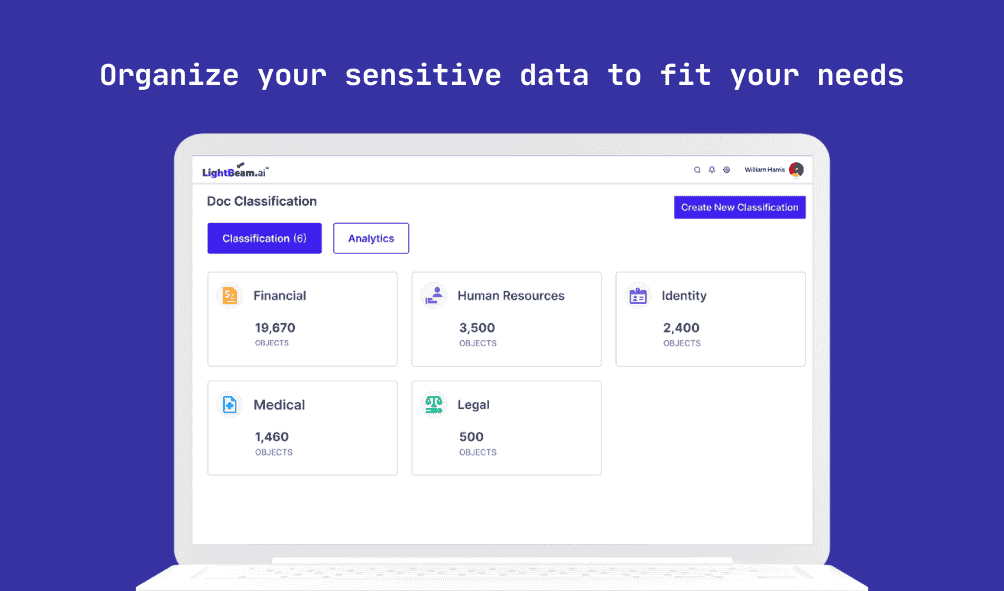
Watch our video to learn how LightBeam helps in Automating Data Classification
2. Implement Identity-Centric Security
Go beyond data location — understand who the data belongs to, who can access it, and why. Identity-context is essential for enforcing meaningful security controls.
How LightBeam Helps: Using patented Data Identity Graph technology, LightBeam maps and secures sensitive data across structured and unstructured sources, including shadow data. It automates data governance, privacy tasks (DSR, RoPA, Consent), and protection through redaction and anonymization, ensuring comprehensive security. LightBeam creates a live map of your data and shows you exactly which users are connected to it—whether they’re internal employees, contractors, or third parties. For every file or data record, you’ll see who owns it, who touched it, and who shouldn’t have access.
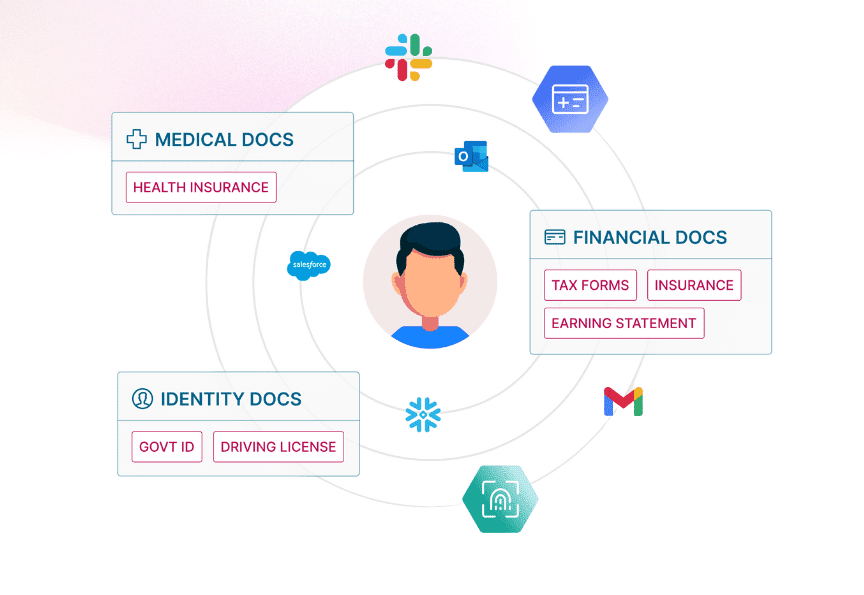
3. Monitor and Secure Shadow Data
Shadow data — unmanaged or forgotten sensitive information — is a silent threat.
How LightBeam Helps: LightBeam continuously uncovers shadow repositories, even in SaaS and multi-cloud environments, and surfaces them for classification and policy enforcement. It also identifies AI-generated shadow data and previously undiscovered data repositories tied to apps like Microsoft Copilot.
🎥 Watch how LightBeam secures Copilot data
4. Automate Risk-Based Access Control
Static roles are not enough. Implement dynamic access policies that adapt based on real-time risk signals.
How LightBeam Helps: Automatically flags and revokes excessive/open/cross departmental access,for overexposed, stale, or orphaned data, reducing insider threats and human error.
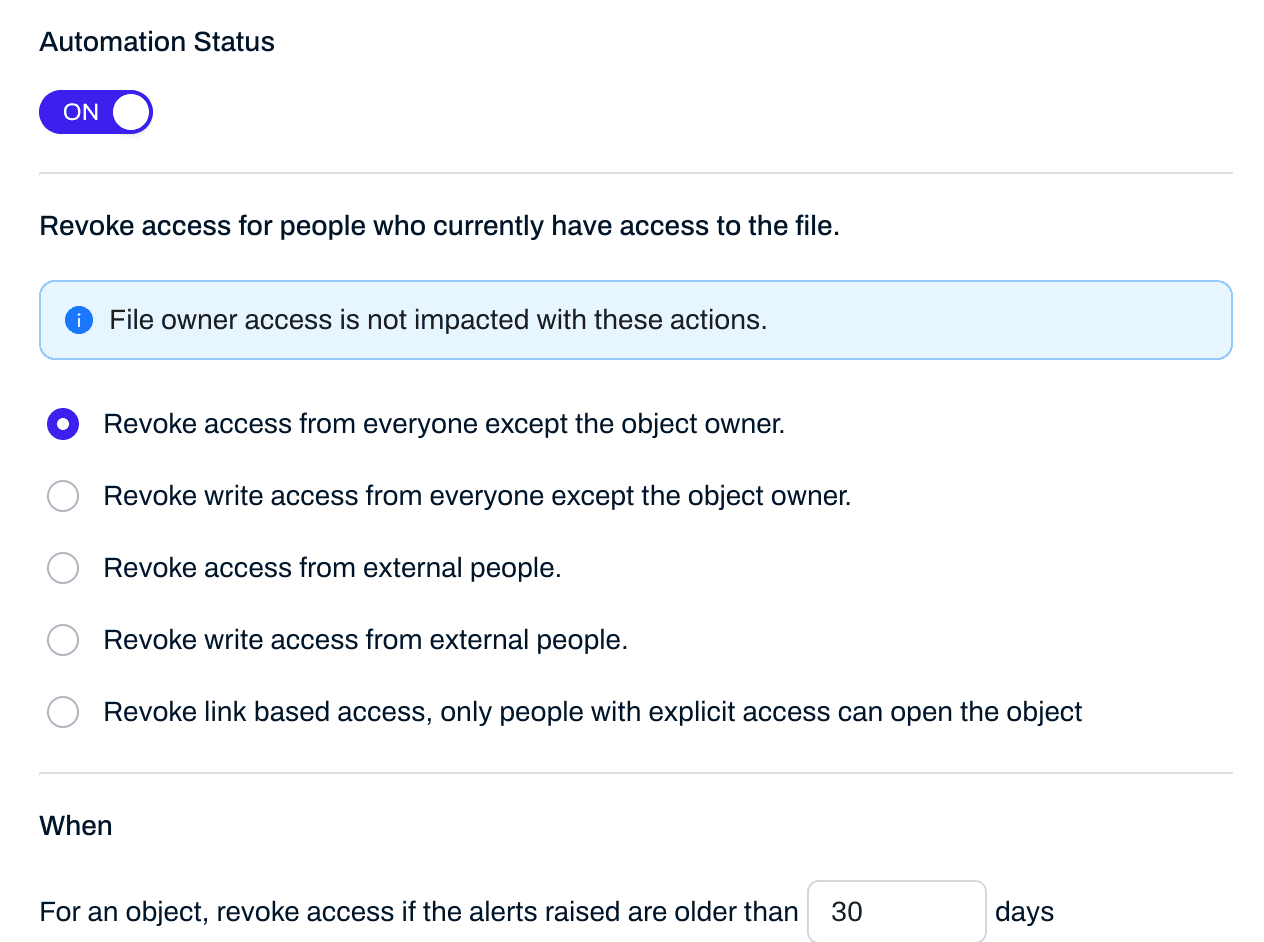
5. Maintain Real-Time Compliance Monitoring
Compliance is not a checklist — it’s a continuous process. Organizations must demonstrate real-time control over sensitive data.
How LightBeam Helps: Enables continuous compliance monitoring for GDPR, HIPAA, CCPA, DPDP, and Quebec Law 25, with real-time audits, RoPA reporting, and breach readiness.
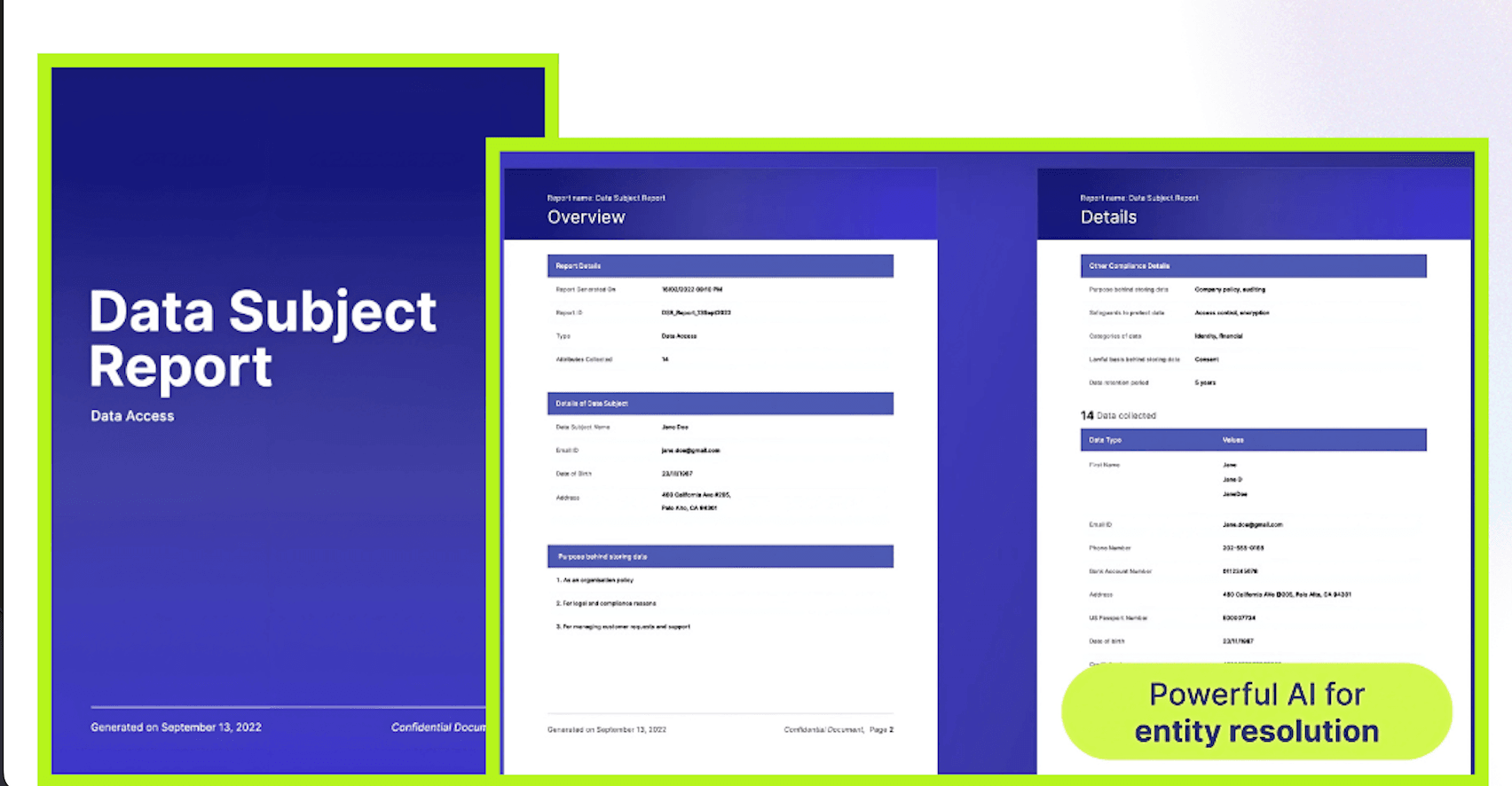
6. Integrate DSPM with DLP
DSPM enhances the effectiveness of existing security tools. Many organizations rely on Data Loss Prevention (DLP) solutions to lower the risk of sensitive data being exfiltrated from the organization. While these solutions offer convenience, they often require significant time and model training before delivering actionable insights and enforcing policies.
How LightBeam Helps: LightBeam solves these challenges while complementing existing DLP and eDiscovery tools. With LightBeam, actionable insights are available within hours, not weeks or months. Our Contextual AI engine enhances accuracy in data discovery and classification, seamlessly integrating with existing data governance frameworks to improve overall DLP accuracy and effectiveness.
Learn More here: Enhancing DLP with LightBeam
7. Enforce Encryption & Data Masking
Even with access controls, encrypting and masking sensitive data adds a critical layer of protection.
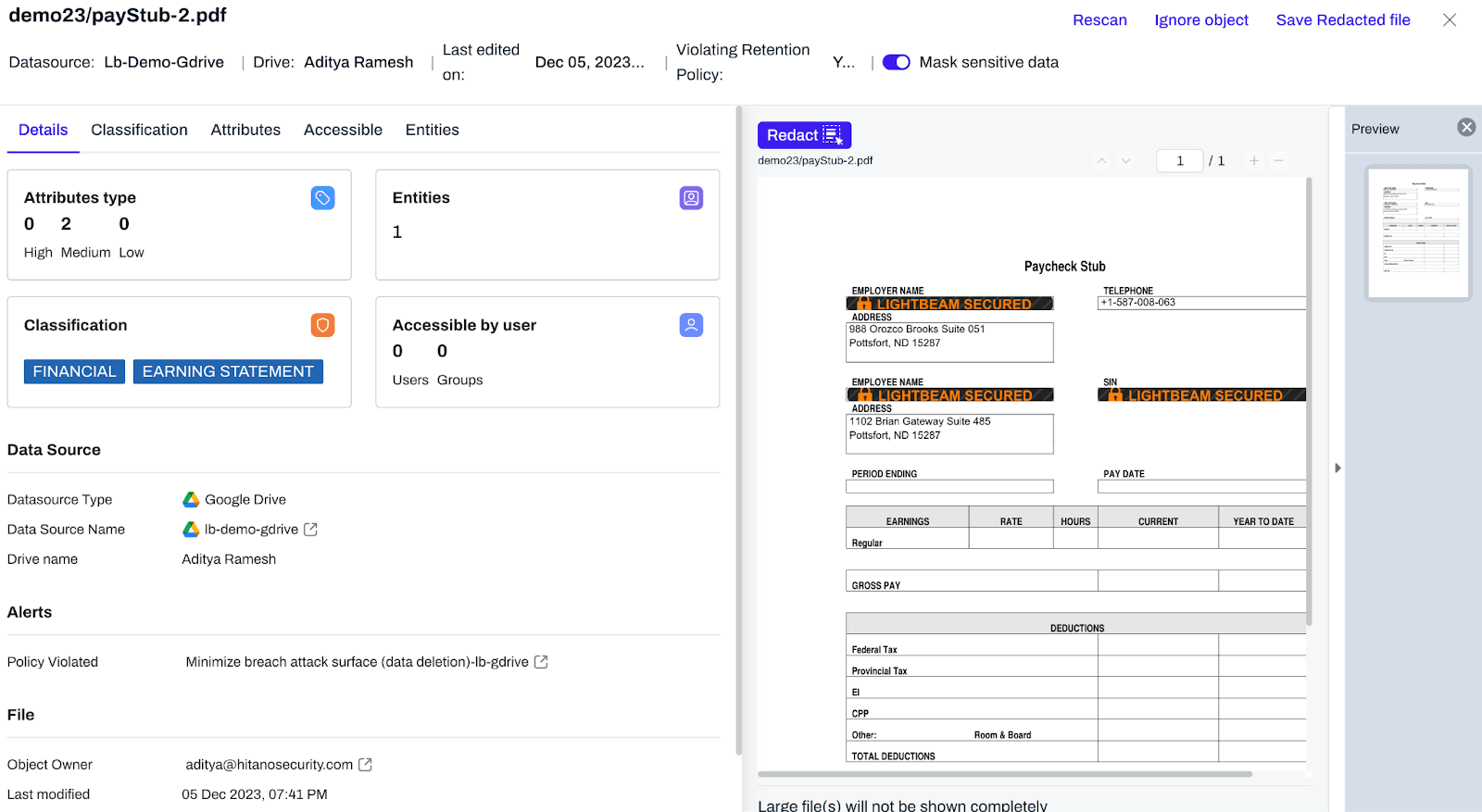
How LightBeam Helps: Automates masking workflows, applying them to sensitive records based on classification and exposure risk through policies and alerts.
8. Continuously Assess Third-Party Risk
very SaaS tool or external vendor connected to your data stack introduces risk, especially when you don’t know what they can see or access. Whether it’s an internal collaboration tool or an external contractor, third-party exposure can lead to data leakage, non-compliance, or worse.
How LightBeam Helps:
LightBeam automatically monitors who your data is being shared with, both inside and outside your organization. It tracks when sensitive data is being accessed by third-party apps, vendors, or employees using platforms like G Suite and Microsoft 365. You get real-time visibility into what data is leaving your environment—emails, files, spreadsheets—and to whom it’s going, so you can act immediately to close risky connections or revoke excessive permissions.
9. Automate Threat Detection & Response
Manual investigation is too slow. Automate threat signals and response workflows.
How LightBeam Helps: LightBeam can help you assess the exposure and prepare a response strategy with just three simple steps aligned with your incident response plan:
– Execute a mutual non-disclosure agreement (MNDA)
– Deploy or connect to LightBeam (with full data residency)
– Identify Impacted Resources, Remediate and Notify Scan the at-risk data sources/repositories to understand the scope of exposure, and generate reports for further action.
Read more about LightBeam’s Breach Response Service here.
10. Use Risk Scoring to Prioritize Remediation
Not all data risks are created equal. Organizations need a way to focus remediation on the most impactful vulnerabilities.
How LightBeam Helps: LightBeam’s Risk Scoring engine analyzes sensitivity, exposure, and access behavior to prioritize threats. Security teams can act faster by focusing on the riskiest users, files, and repositories first.
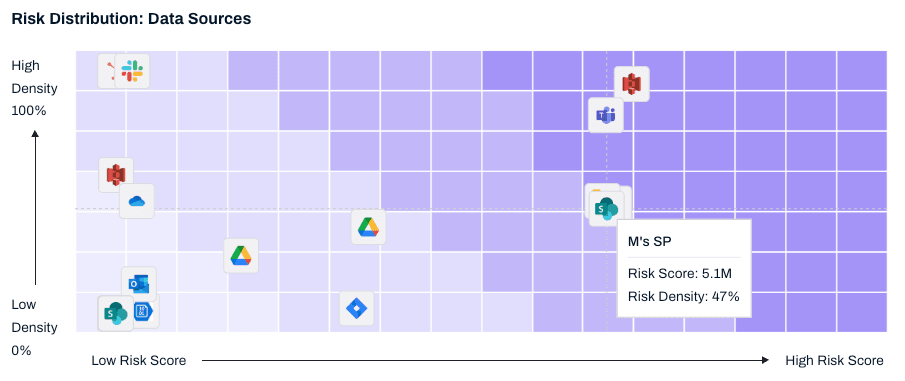
11. Leverage AI and ML for Scalable DSPM
AI-powered DSPM delivers better precision, less manual effort, and faster time to value.
How LightBeam Helps: Employs AI ML-driven data intelligence, risk scoring, and remediation automation to manage thousands of data repositories with minimal human input.
Gartner-Recommended Practices for DSPM
To align with Gartner’s strategic guidance:
- ✅ Define data security policies and posture benchmarks
- ✅ Build an enterprise data map and pipelines
- ✅ Analyze data lineage and access context
- ✅ Identify risks and gaps
- ✅ Create policy-driven alerts and workflows
When combined with LightBeam’s automation and identity context, these practices ensure continuous posture management and readiness.
Future Trends in DSPM
Looking ahead, top innovations will include:
- 🧠 AI-first anomaly detection and response
- ⛨️ Zero-trust data access enforcement
- 🌐 Multi-cloud unified data governance
- ⚙️ Risk prioritization using predictive analytics
Organizations will also adopt consent-aware DSPM to align with global data privacy regulations.
Conclusion
DSPM is no longer a future state — it’s an operational necessity. By following these best practices and integrating them into your broader security stack, you gain:
- Real-time data visibility
- Automated risk reduction
- Continuous regulatory compliance
LightBeam’s identity-centric DSPM offers a fast, scalable way to get there — and stay ahead of evolving threats.
Ready to secure what matters?
Explore DSPM with LightBeam today.
FAQ Section (Snippet-Ready)
1. What are the top DSPM best practices for 2025?
The top DSPM practices include continuous data discovery, identity-centric access controls, automated risk remediation, real-time compliance monitoring, and third-party risk management—essential for proactive data protection in 2025.
2. Why is shadow data a key concern in DSPM?
Shadow data refers to unmanaged or unknown sensitive data stored in SaaS, cloud, or local systems. DSPM uncovers this hidden data to reduce blind spots and prevent accidental exposure or non-compliance.
3. How does LightBeam support DSPM implementation?
LightBeam enables continuous discovery, classification, risk scoring, and automated remediation. Its AI-powered Data Identity Graph links sensitive data to identities for precise enforcement and reporting.
4. How does DSPM improve compliance with regulations?
DSPM platforms like LightBeam continuously monitor for data exposure and compliance violations, supporting frameworks like GDPR, HIPAA, and CCPA with automated reporting, RoPA, and audit readiness.
5. What role does AI play in modern DSPM solutions?
AI enhances DSPM by automating risk scoring, policy enforcement, threat detection, and classification, ensuring real-time, scalable protection without excessive manual effort.
Related Posts

Analyzing the New Hampshire Data Privacy Act
Learn More
Imagine this: A Data Protection platform that seamlessly adapts to your organization's specific needs
Learn More


