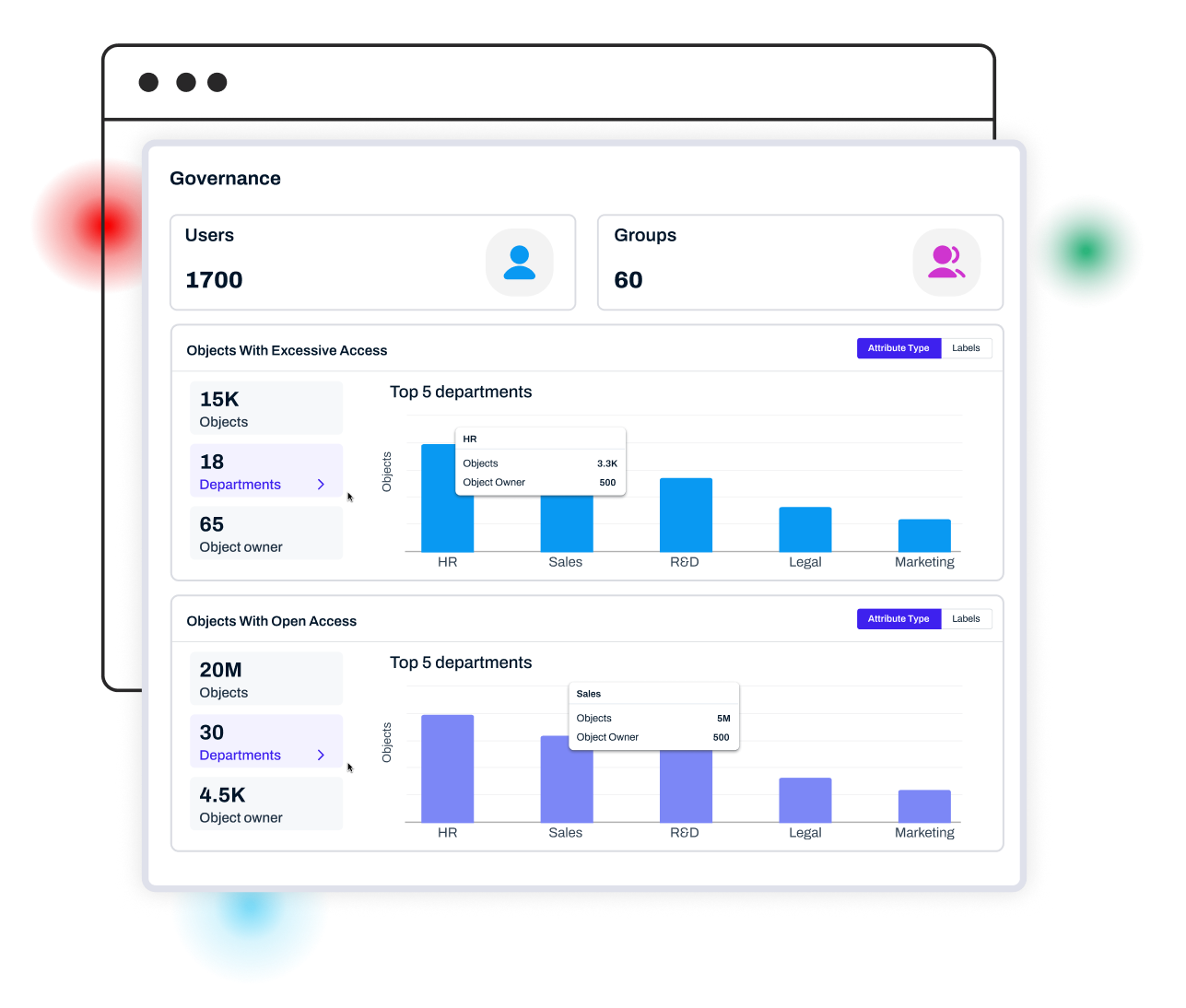
Excessive Access to Sensitive Data Creates Risk and Breaches
Right Size Permissions
Reveal every user or group with excessive sensitive file access, even across S3 and Salesforce models, then revoke permissions automatically.
Stop Third-Party Exposure
Track all sensitive data shared with partners, knowing exactly whose data has been shared and how it’s being accessed.
Pass Audits Confidently
Deliver audit-ready evidence of least-privilege access for all sensitive data, with clear reporting and full context.
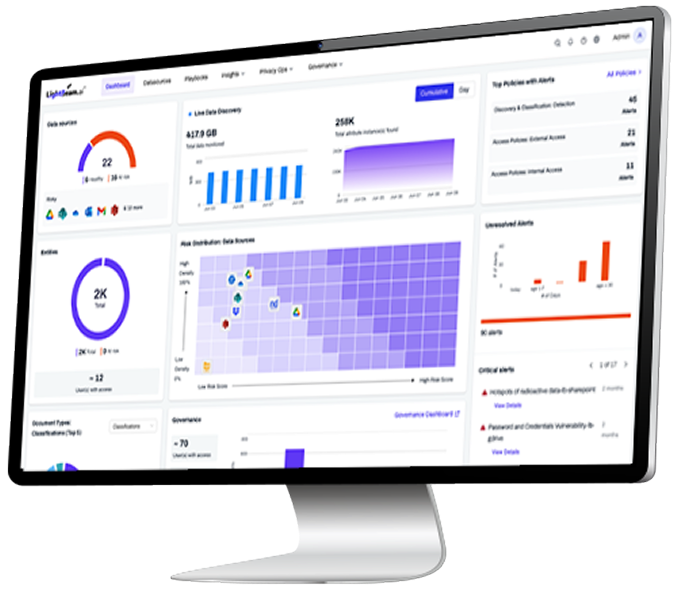
See, prioritize, and fix excessive access in minutes, not months
90%
Reduction in open access
Customers reduced unauthorized access to sensitive data by 90%.
80%
Fewer compliance violations
Decrease compliance violations by 80%, helping organizations avoid penalties.
70%
Faster audit completion
Teams finished access reviews 70% faster with automated reporting.

“It’s easy to use, easy to onboard, and enables everyone to be an owner of client data privacy. This ensures accountability and enables us to always provide the best experience possible for clients.”
David Eddings
President
One platform, context-aware intelligence, zero permission chaos
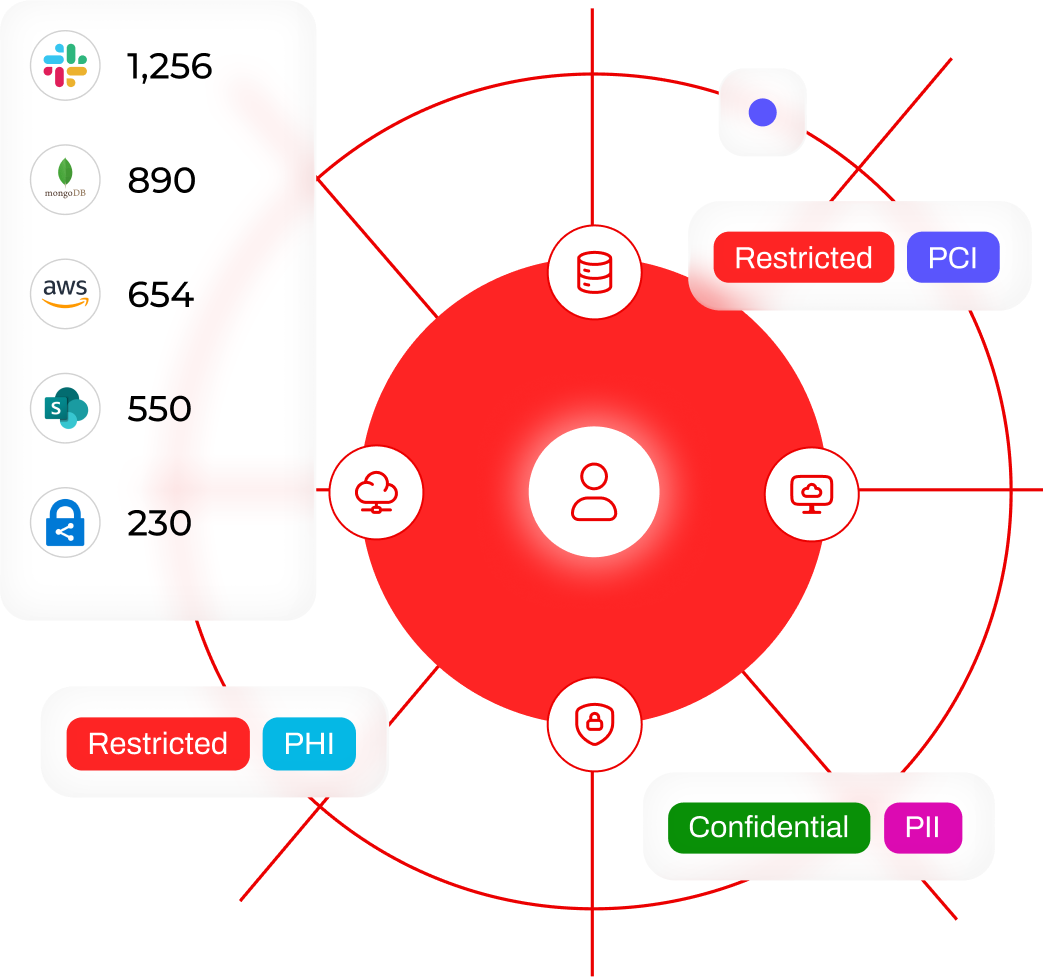
Contextual Visibility
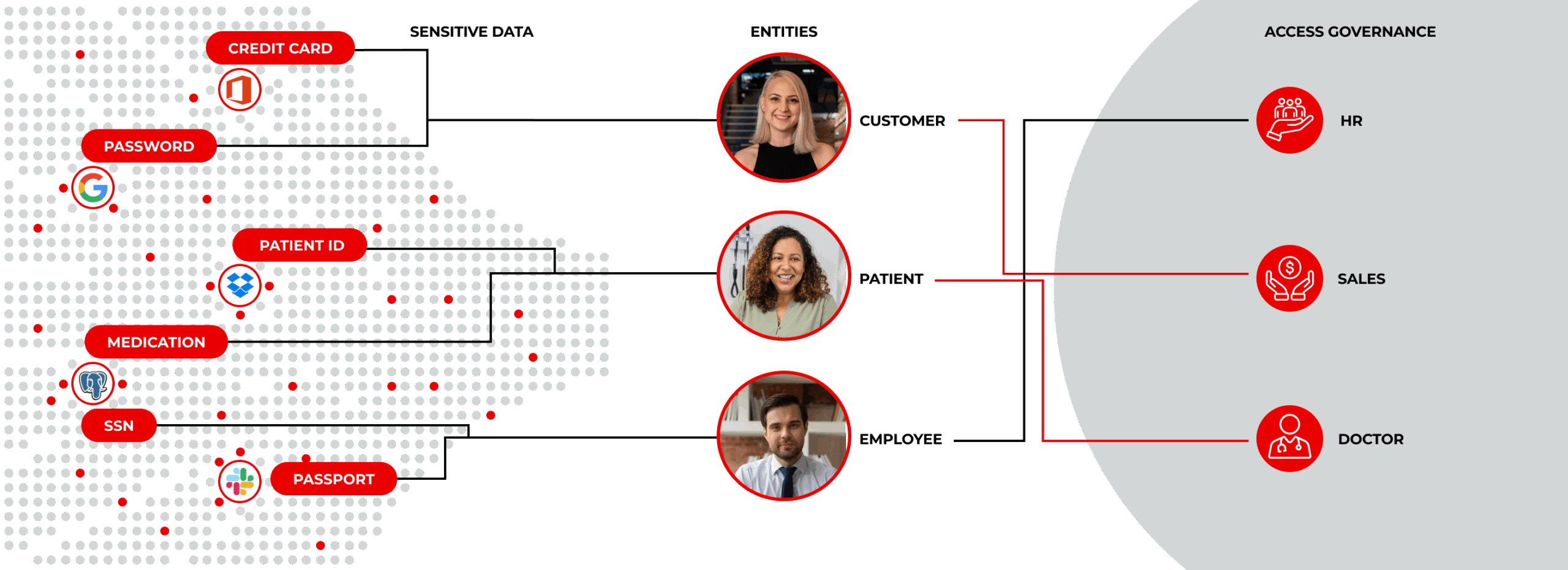
Link every file to the person and business context it represents. The Lightbeam Data Identity Graph shows who has access, why, and how risky that exposure is, with no more blind spots.
Explore Data Identity GraphEffortless Vigilance
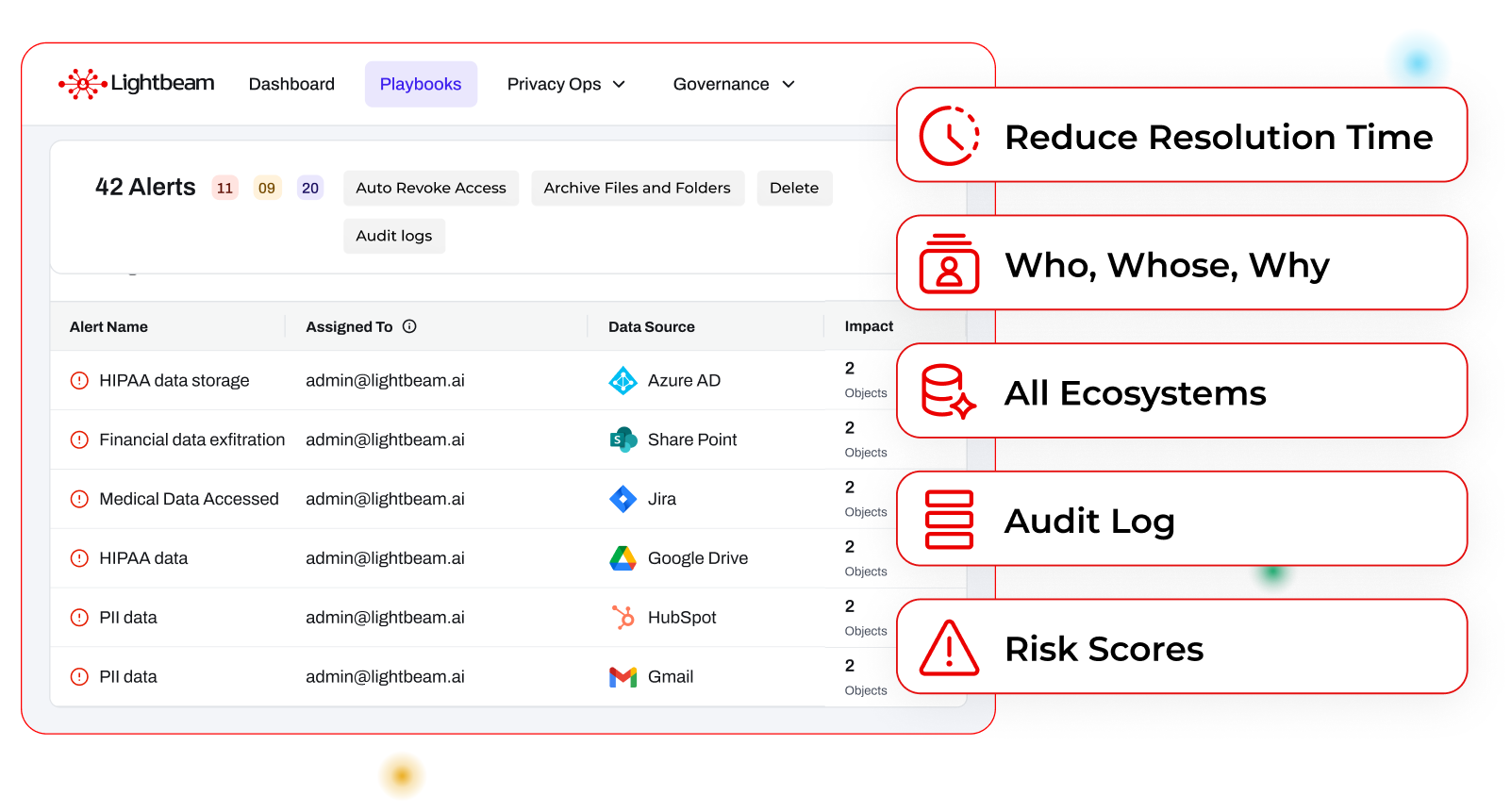
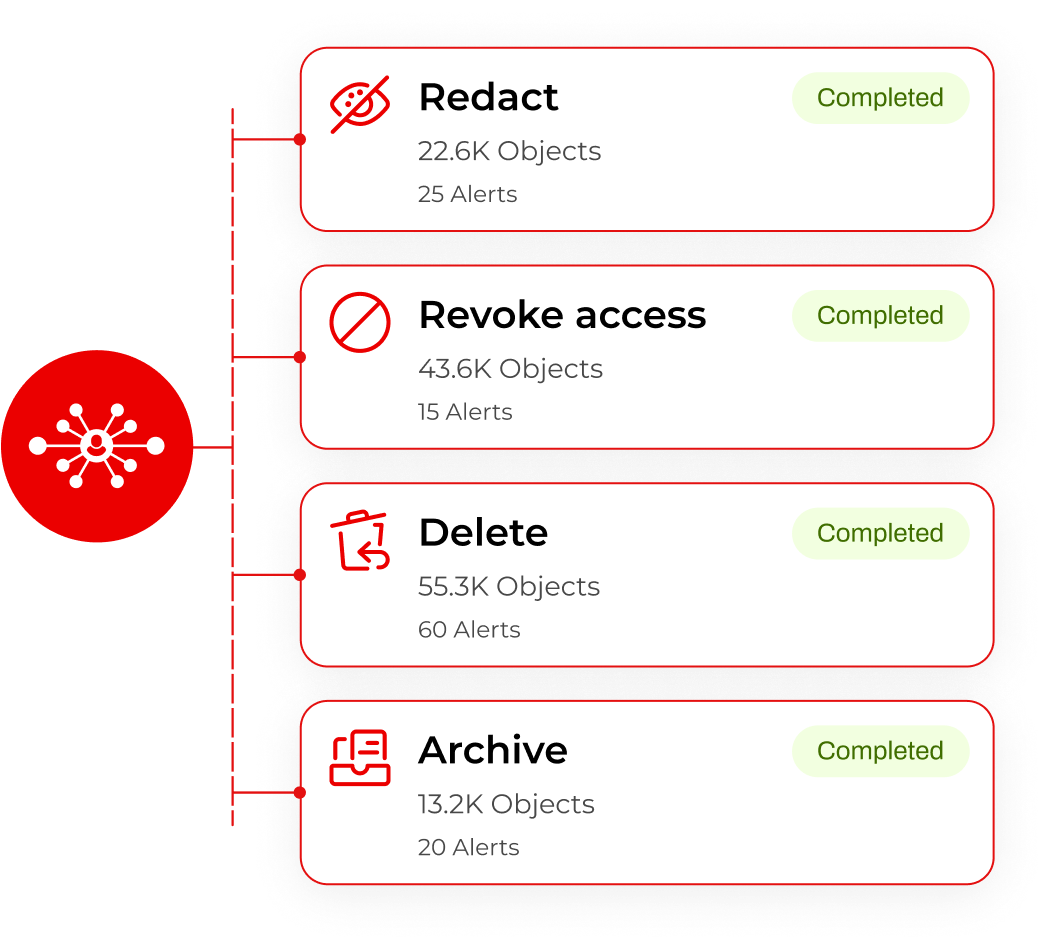
Automated policies revoke open or excessive access when thresholds are crossed, freeing your team for strategy, not chasing alerts. No tickets, just immediate enforcement.
Explore Automated RemediationUnified Governance
Replace siloed tools with one platform that unifies discovery, classification, and access governance. Integrated reports prove compliance and accelerate audits, while cutting cost and admin overhead
Explore Our Platform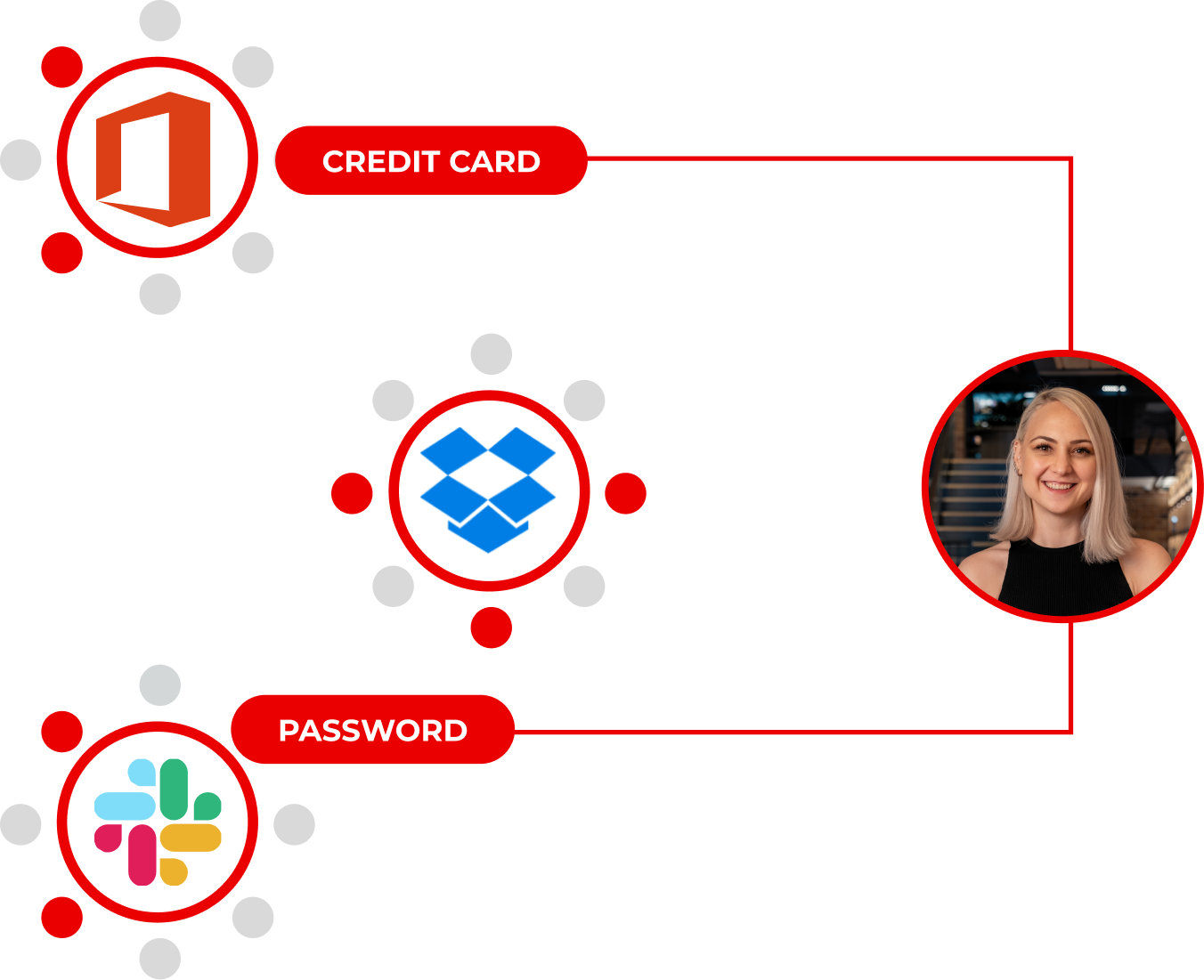
Data Access Governance with Business and Identity Context
Lightbeam discovers sensitive data, analyzes the context, maps identities, flags excessive access, and continuously remediates security risks to enforce least privilege access.
See what else the Lightbeam platform solves
Data Classification
Discover and classify structured and unstructured data, surface risk and reduce exposure at scale.
Learn MoreUser and Entity Behavior Analysis
Lightbeam detects insider risk by baselining user behavior on sensitive data, then flags and remediates threats, showing who’s at risk, what moved, and why.
Learn MoreData Security Posture Management
Lightbeam discovers shadow data, maps risk, and automates remediation so security teams gain clear control and compliance.
Learn MoreRansomware Protection
Lightbeam detects rapid encryption or deletion, then auto-contains threats by revoking access, suspending sessions, and showing who, what, and where in one click.
Learn MoreCustomers who love their results
Quick Answers
Frequently Asked Questions
How is the Lightbeam platform different from legacy file-access auditing tools like Varonis?
Legacy tools scan permissions but ignore data context. The Lightbeam platform links each permission to sensitive content and the person it represents through the Data identity Graph. This reveals who has access to whose data, prioritizes risk, and automates remediation with policy workflows, reducing unauthorized access by up to 90%.
Explore Data Identity GraphCan the Lightbeam platform revoke access automatically when risk thresholds are exceeded?
Yes. Policies watch for open, external, or excessive access. When triggered, the platform changes the permissions at the source, notifies owners, logs the action, and verifies closure. Automation enforces consistency and cuts exposure time drastically.
Explore AutomationWhich repositories does Lightbeam support for Data Access Governance out of the box?
Lightbeam Data Access Governance supports any data source that Lightbeam supports.
View Our Integrations