DSR vs. DSAR: A Guide to Data Subject Requests
Learn the difference between Data Subject Access Requests (DSAR) and Data Subject Rights (DSR), how to respond to a DSAR, and how automation can help organizations meet global privacy compliance requirements.
Bill Schaumann
DSR vs. DSAR: A Guide to Data Subject Requests

What is a Data Subject Request (DSR)?
“Tomato, tomahto / Potato, potahto” is a fun way to say the same thing, only differently. It comes from the song “Let’s Call the Whole Thing Off” by George and Ira Gershwin, performed by Fred Astaire and Ginger Rogers in 1937.
The terms Data Subject Rights (DSR) and Data Subject Access Requests (DSAR) both refer to the same thing—regulatory requirements that give individuals certain rights over their personal data. These requirements are also known by other names, such as Individual Rights Request (IRR) and Patient Access Request (PAR). A multitude of other U.S. and global regulations provide various names, versions, and levels of rights, which allow individuals access to the information being collected, stored, and processed about them by covered entities. These individuals, or Data Subjects, have a variety of rights afforded to them. By implementing the DSR and DSAR process, organizations can meet this regulatory requirement.
What’s the difference between DSR and DSAR?
DSR is commonly used in industry to refer broadly to any formal request from a person about their personal information and includes all of the associated data rights. Each right requires different response activities to be performed by the organization to fulfill the request.
DSAR: The basic individual right that practically all regulations cover is Access. Data Subject Access Request—or the Access right—allows individuals to ask the question, “What data do you have on me?” Although DSAR refers specifically to the Access right, the term has also become a more general label for the overall DSR process.
Common Types of Data Subject Requests
– Access request – “What data do you have about me?”
– Correction request – “Please fix inaccurate data you hold.”
– Deletion request (Right to be Forgotten, Erasure) – “Delete my personal data.”
– Portability request – “Send me my data in a readable format.”
– Objection to processing – “Stop using my data for a specific purpose.”
– Restriction of processing – “Limit how you use my data.”
– Do Not Sell – “Do not sell or trade any of my data for services.”
DSAR Fulfillment Challenges
Fulfilling a DSAR within regulatory timeframes (30 to 45 days) can be complex, especially when personal data is distributed across cloud apps, shadow IT, and third-party systems. Challenges include:
– Identity Verification without collecting new PII
– Accurate Data Discovery across structured and unstructured data
– Minimizing False Positives in classification
– Audit Trail Documentation to prove compliance
The History and Evolution of DSARs
Although HIPAA (the Health Insurance Portability and Accountability Act of 1996) is one of the more well-known U.S. privacy laws containing access rights for patient data, the concept of access to personal information predates HIPAA. In the United States, the Privacy Act of 1974 requires federal agencies to provide access and correction rights to individuals regarding their own digital data.
In 1980, the International Privacy Guidelines were published by the Organization for Economic Co-operation and Development (OECD). This framework included core principles about individuals knowing what data controllers hold about them. Another popular privacy framework, the Generally Accepted Privacy Principles (GAPP) includes an Access domain.
More recently, in 2018, the European Union’s General Data Protection Regulation (GDPR) brought DSRs to the forefront for many data privacy and governance teams. The GDPR increased the types of rights afforded to EU residents and significantly raised the stakes for violations, with fines of up to 4% of an organization’s annual revenue. In the United States, California was the first state to pass similar legislation. The CCPA and CPRA include DSR provisions for their residents.
The CCPA also introduced a new right of “Do Not Sell My Data.” The concept that data has value beyond its transactional function was popularized by the British mathematician and data science pioneer Clive Humbly, who in 2006 said, “Data is the new oil. It’s valuable, but if unrefined it cannot really be used.” A core privacy principle states that personal information should only be used for the originally intended purposes, and the notion of selling data for marketing, or research, or other purposes justifies the principle that without permission from the data subject, personal information should not be sold.
A particularly challenging right introduced by the GDPR was the right to erasure, or the right to be forgotten. “Delete my data” requests can prove difficult to fulfill, as centralized data inventories are not traditionally organized around individual data subjects. Moreover, data subject information is often scattered across a growing and complex digital ecosystem. As a result, GDPR drove renewed focus on understanding whose data is being processed, in addition to what data is processed and where it is stored.
Identity Data Inventory
Today, many organizations deploy a variety of data sources to store and process the transactional data required to operate their businesses. On-premises and cloud-based systems, along with third-party service providers, handle the data of customers, employees, and other data subjects across a broad array of applications and databases.
Responding to a DSR requires locating and compiling all data related to an individual into an accurate and complete picture. It is also important to understand why the data exists and what is the legal basis for processing it. This is a difficult task without the technical capabilities to identify, categorize, synthesize, and document the data being processed.
The DSAR Fulfillment Process: Step-by-Step
Solving the challenge of co-referencing fragmented data and building an identity-centric PII graph for each entity requires understanding what data is stored and where. API connections to data sources, combined with scanning and logical data assimilation tools, are essential to fulfill a request. However, data discovery and documentation inventory is only part of the broader DSR process.
Taking in a request and fulfilling it in a timely manner requires support across the organization—from customer service to technical teams, and legal reviewers. A structured enterprise workflow can streamline and automate the process.
There are six distinct steps in fulfilling a DSR:
– Receiving and validating the request
– Validating the requestor
– Discovering the requester’s data
– Assembling the output report
– Approving the report
– Communicating with the requester
Receiving and Validating the Request
The first step is to build a request template or form and place a link to it within the public-facing privacy notice, along with appropriate language for the type of request being supported. Once received, the request can be validated for fulfillment.
Validating the Requestor
Confirming the identity of the requestor is a critical step. Ensuring the right data is shared with the right individual helps to maintain privacy and compliance and eliminate unnecessary breaches of personal information. Typically, the requestor can verify their identity by using data the organization has already collected. New or previously uncollected data should not be used for this step.
Discovering the Requestor’s Data
Ever-increasing data and tool sprawl has made it increasingly difficult for IT teams to accurately identify, classify, label, and control sensitive business data across disparate systems of varying data types (structured, unstructured, and semi-structured). Traditional tools for classification rarely take into account the context of a data attribute, often leading to misclassification. Manually reviewing and correcting misclassification is time-consuming and also error-prone.
Because of this, creating the PII Identity graph is often the most challenging part of the process. Accurately identifying what data has been collected from the requester requires a comprehensive understanding of the organization’s systems, processes, and data elements. By connecting to and scanning data repositories, an accurate identity graph for each individual can be created.
Assembling the Output Report
Once the report template is built and the data to be included in the access response is selected, a formal report can be generated for review and approval. Approval authority varies by organization, but it’s essential that the report be accurate and that the data is shared only with the verified requestor.
Communicating with the Requester
Clear communication with the requester is essential throughout the process, from initial receipt to final delivery of the report or outcome. Effective communication helps build trust and ensures the requester is informed every step of the way. Automated communications for each step are prepared in advance and triggered as part of an automated workflow.
Why Automating DSARs Matters
Responding to requests from customers, consumers, employees, and other population types in a timely and accurate manner is not only a regulatory requirement, but also an important process to create and maintain brand loyalty. Organizations that can respond to requests effectively will meet the expectations of their constituents and regulators.
Manual handling of DSRs is inefficient, risky, and prone to delays. Automating DSRs can;
– Reduce time and cost of fulfillment
– Improve accuracy through identity graphing
– Support audit trails for compliance
Building and operating a collaborative automated DSR process is now possible by deploying privacy and security solutions provided by LightBeam.ai.
Data Subject Request (DSAR/DSR) under GDPR vs. CCPA: What’s the Difference?
In today’s data-driven world, individual privacy rights are increasingly becoming a focal point of regulatory frameworks. Two of the most influential data protection laws globally—the General Data Protection Regulation (GDPR) in the European Union and the California Consumer Privacy Act (CCPA) in the United States—both provide individuals with the rights regarding personal data. These rights are typically exercised through a Data Subject Request (DSR). However, the scope and execution of DSRs under GDPR and CCPA differ significantly.
Data Subject Request (DSR) under GDPR
Jurisdiction: European Union (and any organization processing the data of EU residents)
Scope of Data: Includes all personal data—structured and unstructured—that can identify a data subject.
User Eligibility: Any data subject (citizen or resident) within the EU, for business conducting operations in the EU, regardless of where the organization is based.
Time to Respond: 30 days, with a possible extension of 60 more days for complex requests.
Key Rights Related to DSR:
Right of access
Right to rectification
Right to erasure (right to be forgotten)
Right to data portability
Right to object to processing
Right to restrict processing
Verification Requirements: The organization must verify the identity of the requestor but must not collect additional data unnecessarily.
Penalties for Non-Compliance: Up to €20 million or 4% of global annual revenue, whichever is higher.
Data Subject Request (DSR) under CCPA
Jurisdiction: California, USA
Scope of Data: Personal information that identifies, relates to, or could reasonably be linked to a consumer or household.
User Eligibility: California residents and businesses (even if temporarily out of state).
Time to Respond: 45 days, with an additional 45-day extension allowed if reasonably necessary.
Key Rights Related to DSAR:
Right to know what personal information is collected
Right to access personal data
Right to deletion
Right to opt out of the sale of personal information
Right to non-discrimination for exercising privacy rights
Verification Requirements: Businesses must use reasonable methods to verify the identity of the consumer.
Penalties for Non-Compliance: Up to $7,500 per violation (enforced by the California Attorney General or CPPA).
Feature
GDPR
CCPA
Geographic Scope
Global (If offering goods and services in the EU or processing EU resident data)
California-based organizations with >25m in revenue or 100k + CA resident data.
Data Coverage
Broader: any personal data
Narrower: Personal data linked to an individual, or the categories of data being held.
Data Subjects
Residents of the EU
Consumers, employees, applicants, contractors, and B2B contacts.
Processing Entities
Data controllers and processors
For-profit entities meeting certain thresholds
Rights Covered
Access, correction, deletion, portability, objection, restriction
Access, deletion, opt-out of sale, non-discrimination
Compliance Strategies for GDPR and CCPA
Regardless of the regulation, the fundamental steps to fulfill a DSAR are similar but must be adapted to specific requirements:
1. Intake Mechanism: Provide a user-friendly web form or email address for submitting requests. Ensure it’s prominently visible in your privacy notice.
2. Identity Verification: Adopt multi-factor methods for GDPR and reasonable verification for CCPA. Avoid collecting excessive new data.
3. Data Discovery: Use tools that can scan structured and unstructured data repositories to find the personal information of verified requestors.
4. Report Assembly: Consolidate the discovered data into an understandable format tailored to the legal requirements.
5. Approval and Delivery: Secure internal review before sharing the report with the verified requestor.
6. Audit Trail: Maintain clear communications with the requestor and logs for all requests and actions taken to support audit readiness.
Global Implications: Privacy is Global
The GDPR and CCPA are just the tip of the iceberg. Data privacy regulations are rapidly proliferating across the globe. In fact, 75% of the world’s population is now covered by some form of privacy legislation. Companies must look beyond the EU and California and prepare for a patchwork of global compliance.

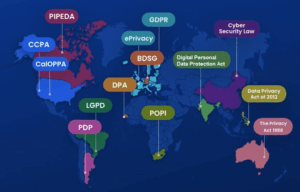
Country/Region
Law/Regulation
Access Right?
Other Rights
European Union
GDPR
Yes
Correction, Deletion, Portability, Objection, Restriction
United States
CCPA/CPRA (California)
Yes
Deletion, Opt-Out, Non-Discrimination
Canada
PIPEDA
Yes
Correction, Consent
Brazil
LGPD
Yes
Correction, Deletion, Portability
India
DPDP Act (2023)
Yes
Correction, Grievance Redressal
South Africa
POPIA
Yes
Objection, Correction
Australia
Privacy Act (amendments pending)
Yes
Limited additional rights
Colorado
Colorado Privacy Act
Yes
Deletion, Portability, Opt-Out
Virginia
Virginia Consumer Data Protection Act
Yes
Correction, Deletion, Opt-Out
Connecticut
CTDPA
Yes
Deletion, Portability, Opt-Out
How LightBeam.ai Helps with DSAR Compliance
LightBeam is an identity-centric data security solution that reduces breach risks, ransomware costs, and regulatory penalties by converging DSPM, privacy, and governance into a single AI-driven platform. Powered by patented Data Identity Graph technology, LightBeam discovers and maps sensitive data across structured, unstructured, and semi-structured sources—including shadow data—linking it to business context and human identities. This enables organizations to enforce governance policies, automate privacy workflows (DSR, RoPA, Consent), and reduce risk through precise redaction, archival, deletion, and access governance.
Watch how you can automate your DSR with LightBeam
Manually fulfilling DSRs is time-consuming, error-prone, and unsustainable as request volumes rise. That’s where LightBeam.ai comes in.
Here’s how LightBeam simplifies DSR compliance:
Automated Discovery: Scans structured, unstructured, and semi-structured data across on-prem and cloud environments.
Identity Graph Technology: Links sensitive data back to the individual across all systems, creating a centralized identity view.
Workflow Automation: Orchestrates the intake, verification, discovery, and report assembly steps through automated workflows.
Real-Time Audit Logging: Maintains detailed audit trails for every DSAR handled, simplifying regulatory reporting.
Shadow Data Protection: Identifies and secures sensitive data in overlooked repositories.
Customizable Templates: Pre-built collection forms and response templates for both GDPR and CCPA compliance.
Benefits of using LightBeam
– Lowers the cost and time to perform data subject requests (DSR), Privacy Impact Assessments (PIA), ROPAs and consent management.
– Improve customer service by replying to privacy related information requests instantly.
– Unmatched Accuracy: Ensuring precise discovery, classification, and labeling of sensitive data
– Comprehensive Shadow Data Protection: Identifies and secures sensitive data in shadow repositories, significantly reducing the risk of unauthorized exposure and potential breaches.
– LightBeam precisely identifies affected customers and employees in a breach, enabling fast, targeted response.
Read more in detail here.
Conclusion
While both GDPR and CCPA empower individuals with rights regarding their data, the mechanisms and obligations they impose on businesses differ in crucial ways. Understanding these nuances is vital for compliance, operational efficiency, and brand trust.
Organizations must invest in scalable, automated solutions to manage growing volumes of DSARs across evolving global regulations.
Ready to simplify your DSR process?
➡️ Request a demo with LightBeam.ai and see how you can automate data subject requests with confidence.
FAQ Section
– What is the difference between a DSR and DSAR? A DSR refers to any data subject right, while a DSAR specifically refers to access to personal data.
– What laws require DSAR compliance? GDPR, CCPA, CPRA, HIPAA, and others mandate the right of access via DSARs.
– Can DSARs be automated? Yes. Automation tools like LightBeam significantly streamline the DSAR fulfillment process.
– How long do I have to respond to a DSAR? Typically, 30 days under GDPR and 45 days under CCPA/CPRA.
– What happens if I fail to fulfill a DSAR? Organizations may face significant fines and reputational damage.
Related Posts

Common Challenges and Mistakes when fulfilling DSRs (Data Subject Requests)
Learn More
CFPB Rule 1033: What Financial Institutions Must Know to Stay Compliant
Learn More


