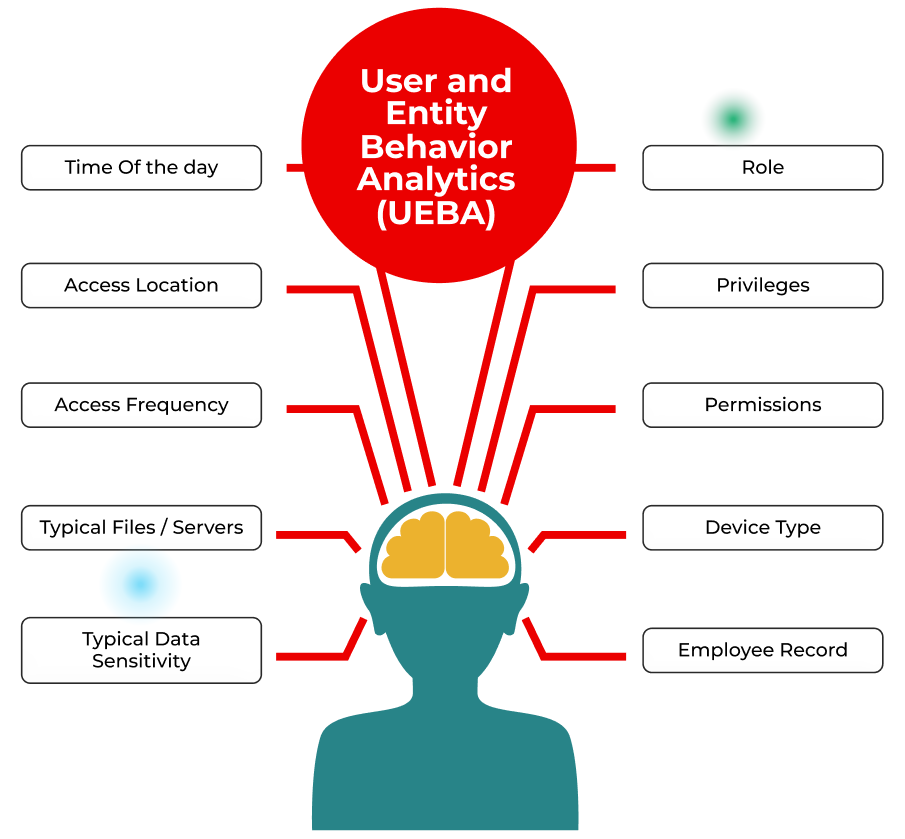
Overview
Insider threat protection with real context
Legacy UEBA floods teams with noise. Lightbeam learns norms, links anomalies to whose data is at risk and then acts in one console.
The Lightbeam Advantage
-
Identity-centric baselines
Per‑user norms enriched with sensitivity and access policies to cut false alarms.
-
From alert to action, fast and precise outcomes
Suspend sessions or revoke access via automated policy playbooks in the same console.
-
Ransomware early warning
Detect write spikes and encryption bursts; auto‑contains compromised user accounts.
-
Access context, instantly
See whose data is touched and the blast radius to target response.
Traditional Industry Approach
-
Static thresholds
One‑size alerts miss intent and bury teams in manual triage.
-
Siloed detection tools delay action and evidence
Separate UEBA and governance delay action and lose audit trails.
-
Missing identity context and intent clarity
Events ignore people and permissions behind risky file activity.
-
Manual containment
Analysts script fixes while damage spreads across shares and apps.
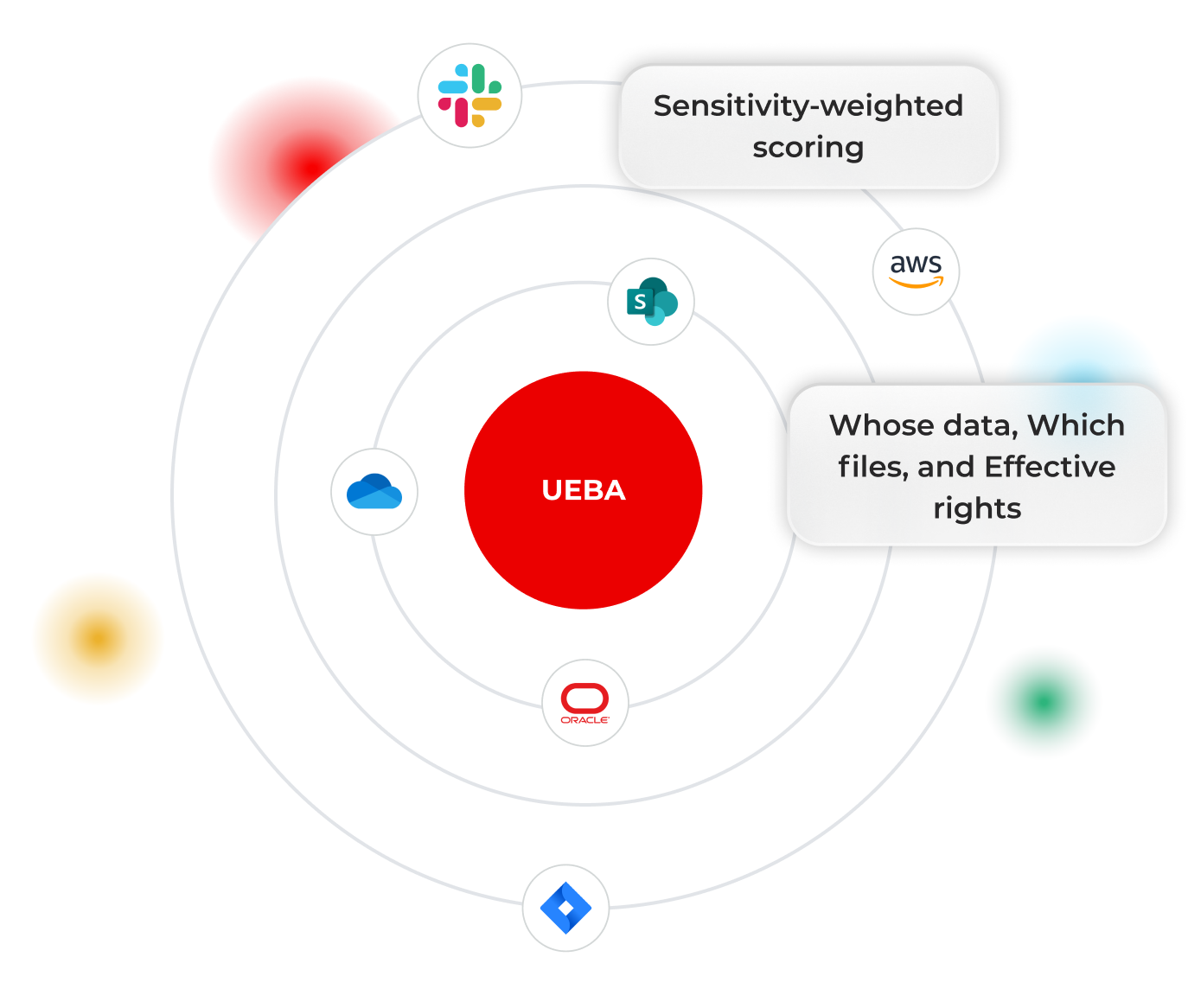
UEBA that knows whose data is at risk, and fixes it fast
Detect true anomalies with sensitivity‑weighted scores and identity context.
Lightbeam builds per‑entity baselines for reads, writes, and access, then scores deviations by data sensitivity and effective entitlements. Alerts show who, what, and whose data is at risk, shrinking investigation time. Trigger playbooks to suspend sessions, revoke access, or quarantine files, without leaving the UI.
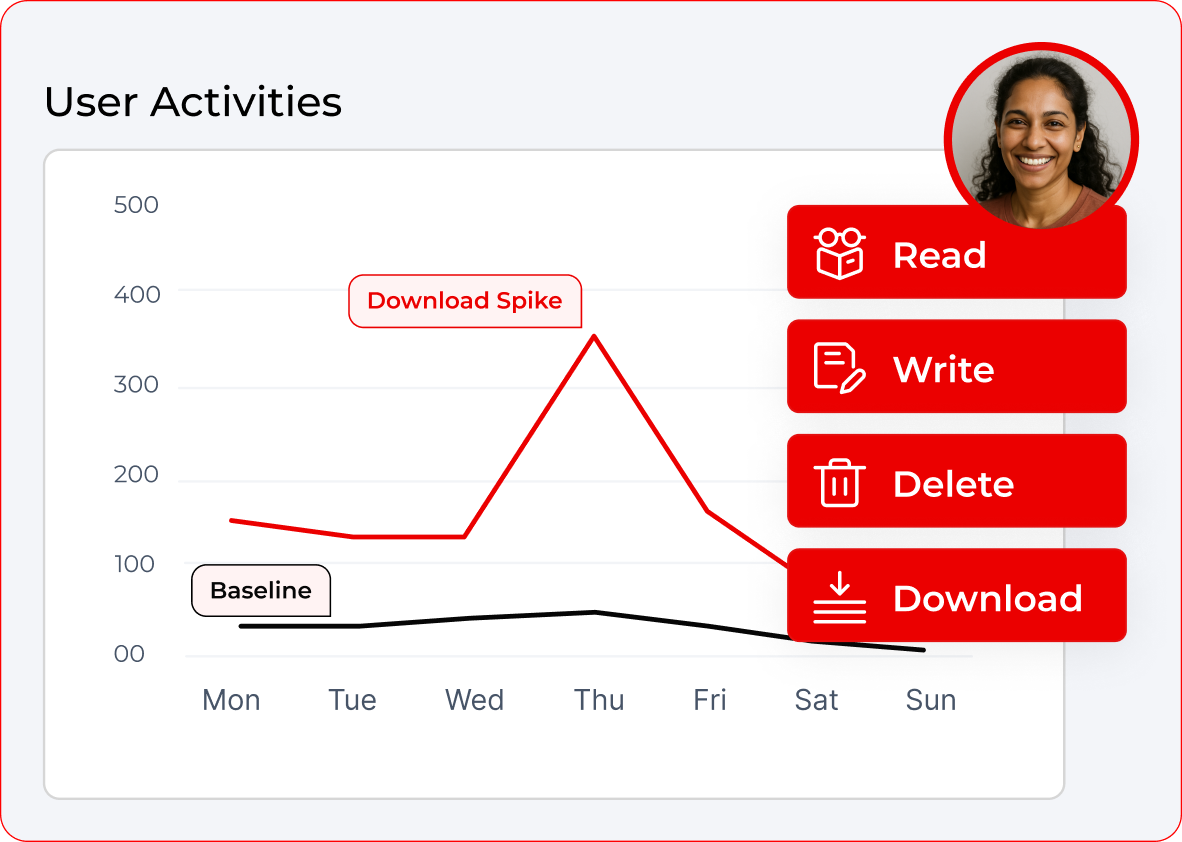
From insider exfiltration to ransomware, contain the blast radius in minutes.
Detect mass downloads, odd‑hour access to sensitive folders, or encryption bursts. Because UEBA is tied to Access Governance, response is decisive: lock accounts, revoke shares, or snapshot impacted paths with an audit trail leaders trust. Identity‑centric context shows exactly whose data is at risk, turning chaos into closed‑loop control.
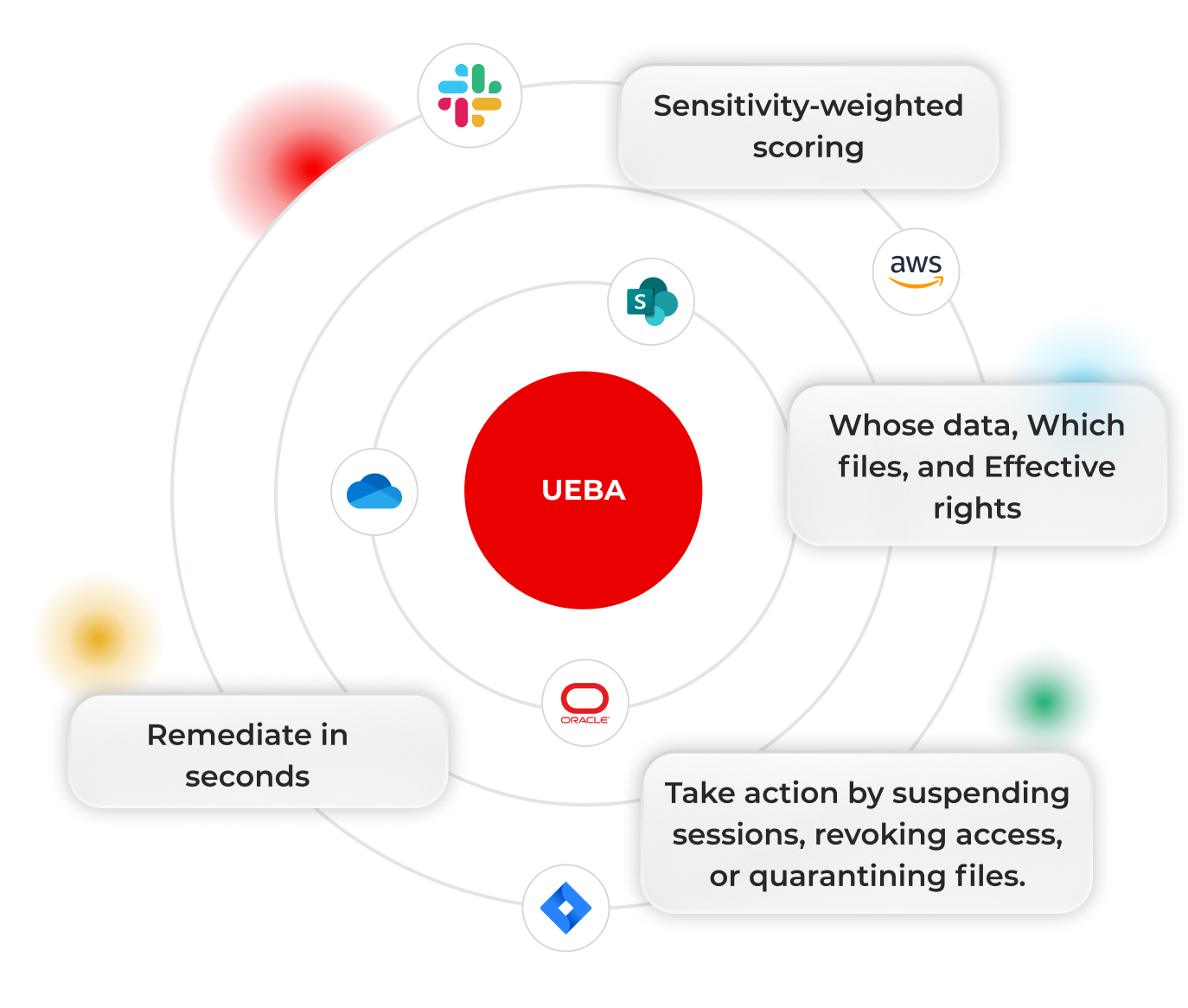
Cut noise, see impact, and remediate in one click, automatically
Detect what matters
Sensitivity‑weighted scoring elevates real threats first, not routine spikes, so teams focus fast
Know the blast radius now
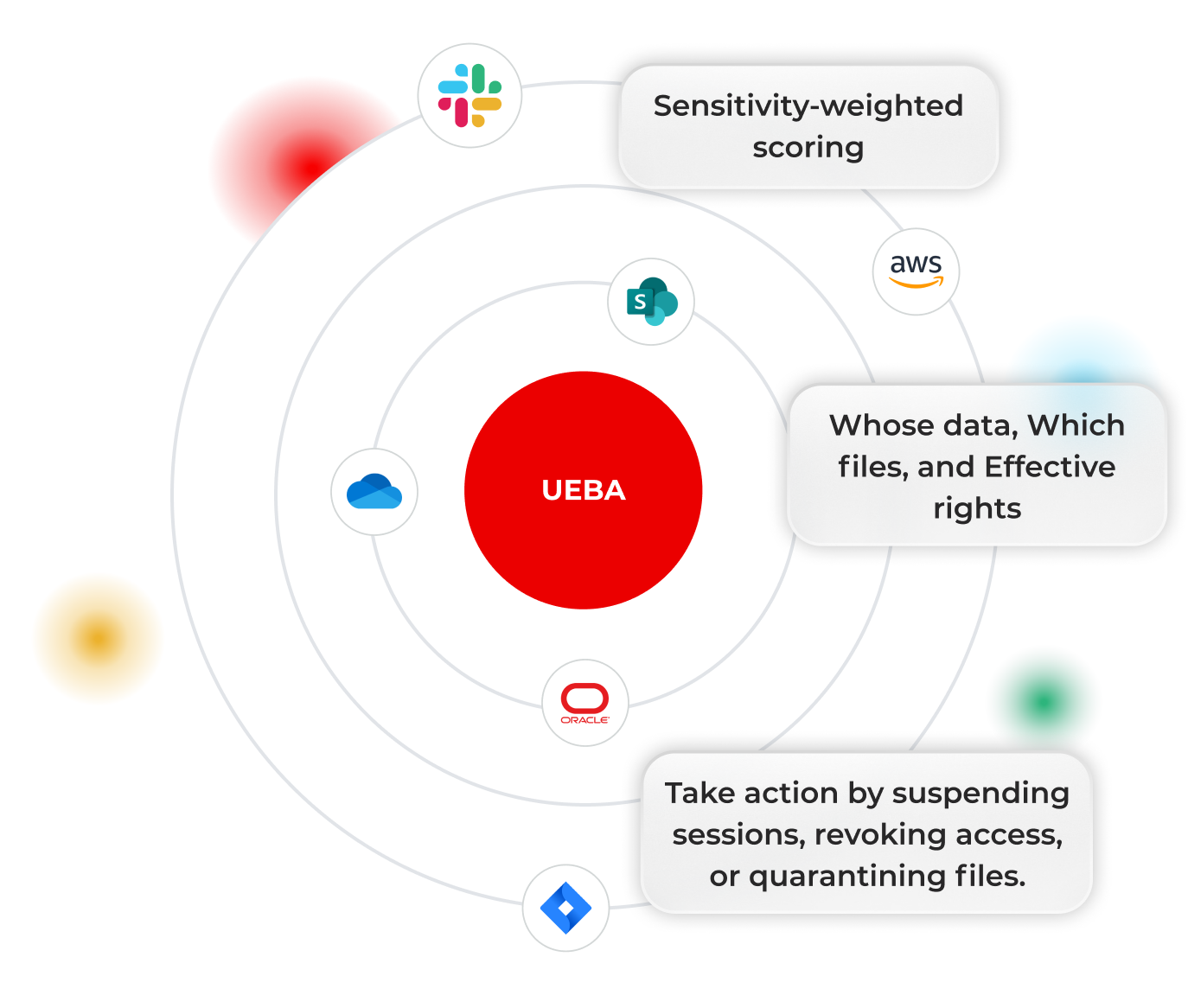
Each alert shows whose data, which files, and effective rights, so impact and intent are immediately clear
Act without friction
Suspend sessions, revoke access, or quarantine files from the same console with audit‑ready logs.
Stop ransomware fast
Spot write surges and encryption fingerprints; auto‑contain compromised identities in seconds.
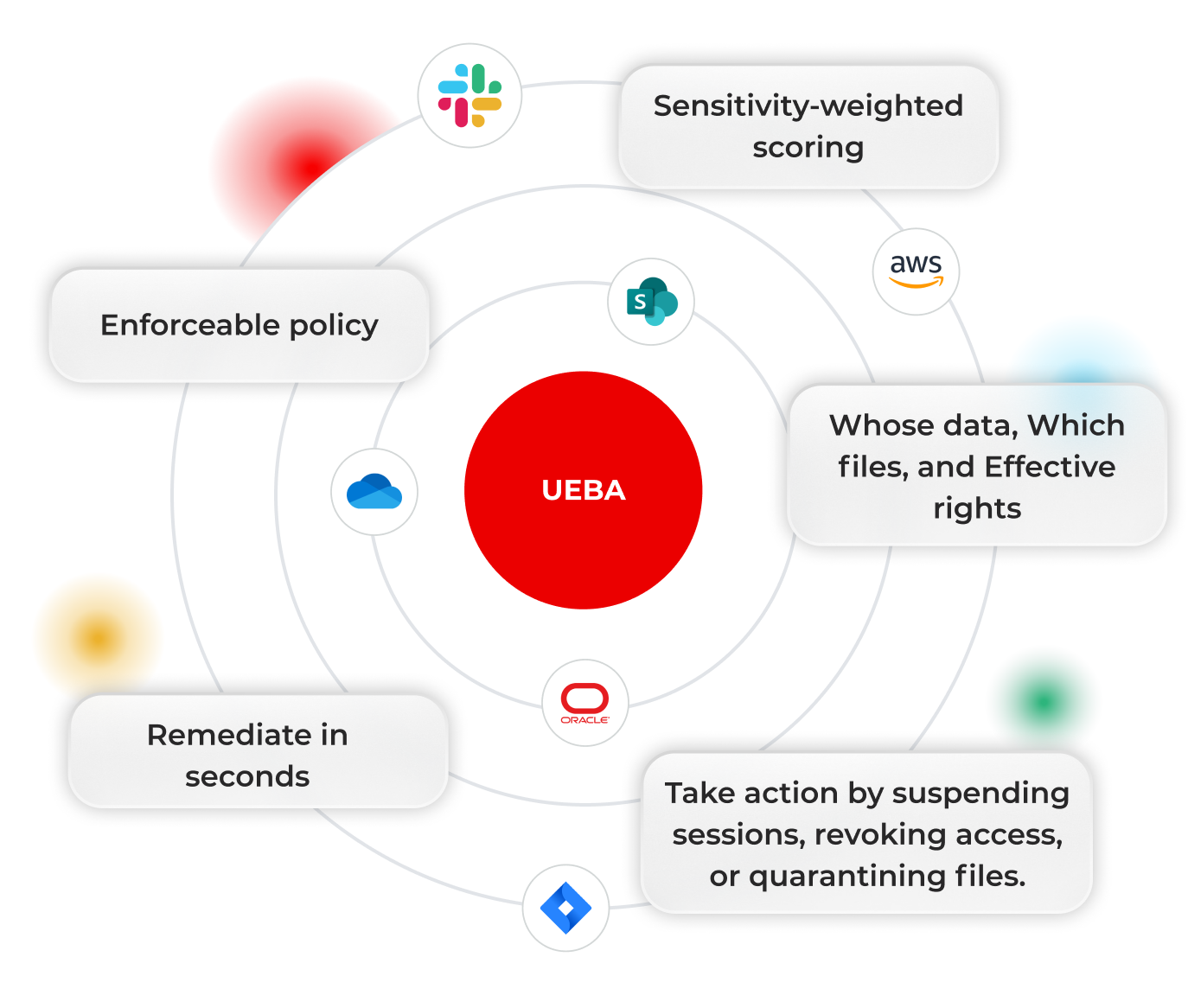
Prove least privilege now
UEBA connects to Access Governance and reviews, turning behavior into enforceable policy and proof.
What customers say
FAQs
Frequently Asked Questions
How is Lightbeam UEBA different from traditional anomaly detection tools ?
Traditional tools stop at alerts. Lightbeam enriches anomalies with identity, sensitivity, and effective‑access context, then triggers policy playbooks to suspend sessions, revoke access, or quarantine files, closing the loop with audit‑ready evidence.
See UEBA in action right nowCan Lightbeam detect ransomware behavior across SMB and collaboration apps?
Yes. The platform learns normal write/delete cadence per user and flags velocity spikes and encryption fingerprints across SMB, SharePoint, OneDrive, and more, enabling one‑click or automated containment.
Explore RansomwareHow does UEBA support least‑privilege and com pliance initiatives?
UEBA signals flow into Access Governance and scheduled reviews, so anomalous behavior leads to rights cleanup and provable attestations. Exportable logs and reports help with SOC 2, ISO, and PCI evidence.
Read the Summer Release BlogBrowse Key Resources

Blog
Summer Release 2025: Stop Ransomware Faster, Spot Insider Risk Sooner, and Prove Access is Correct
News
LightBeam Locks Down Copilot as New Front in Ransomware and Insider Risk Emerges
New release introduces AI Security and governance for Microsoft Copilot, behavioral containment, and UEBA to...