Overview
Stopping Insider and Ransomware Threats
Limited visibility into who can open sensitive data, manual access reviews, and slow response to ransomware, insider risk, and Copilot oversharing keep exposure high.
The Lightbeam Advantage
-
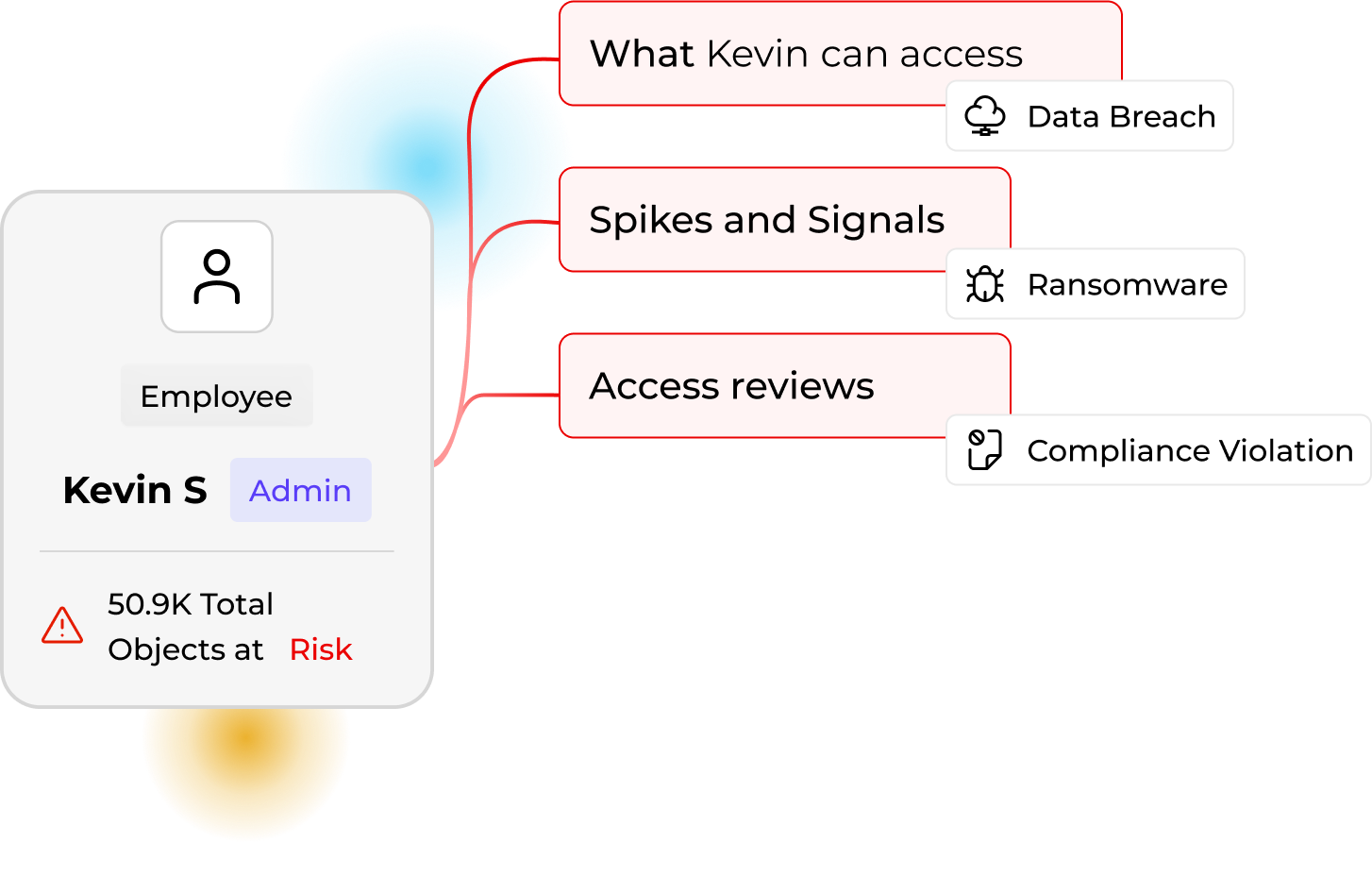
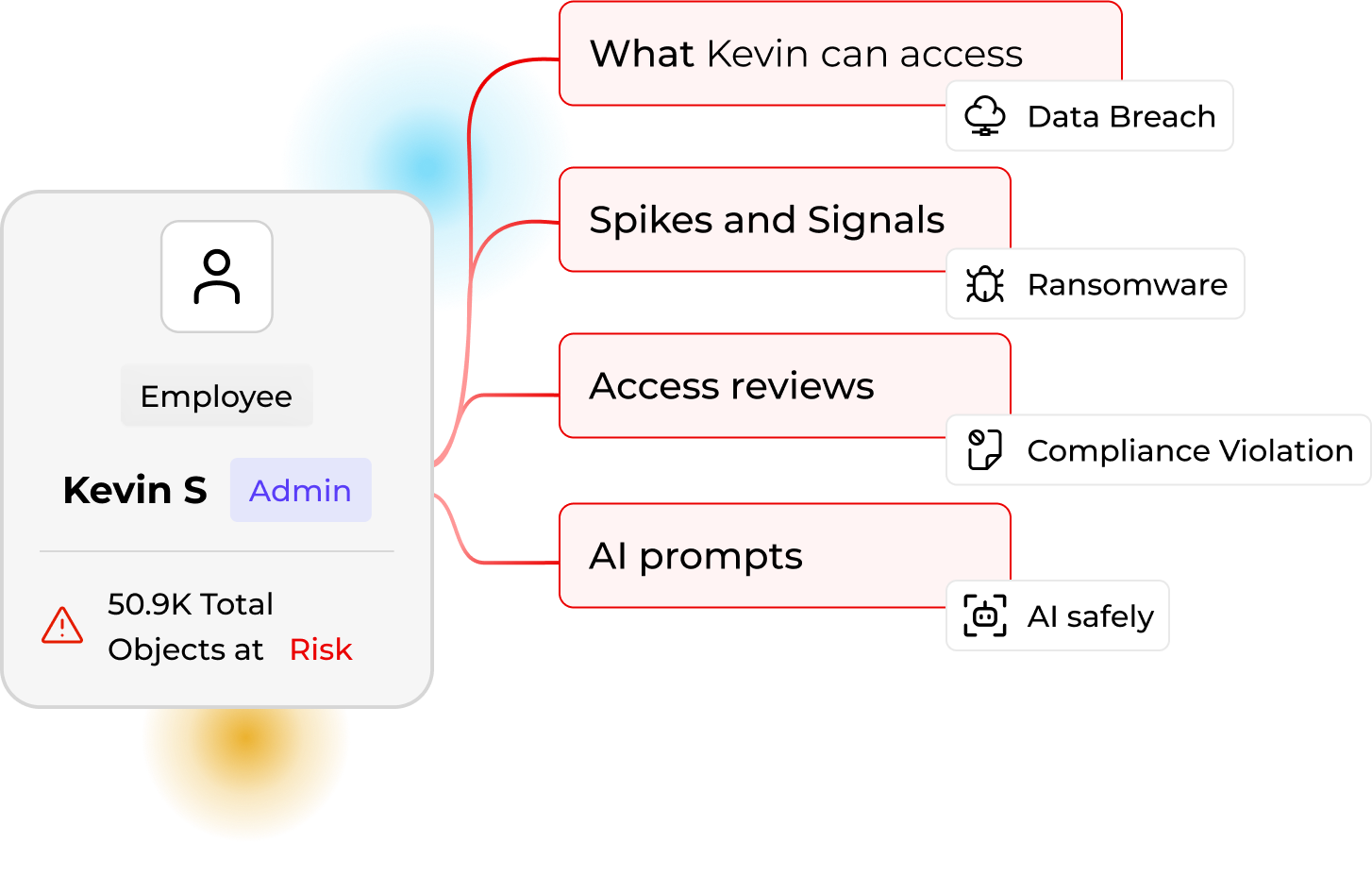
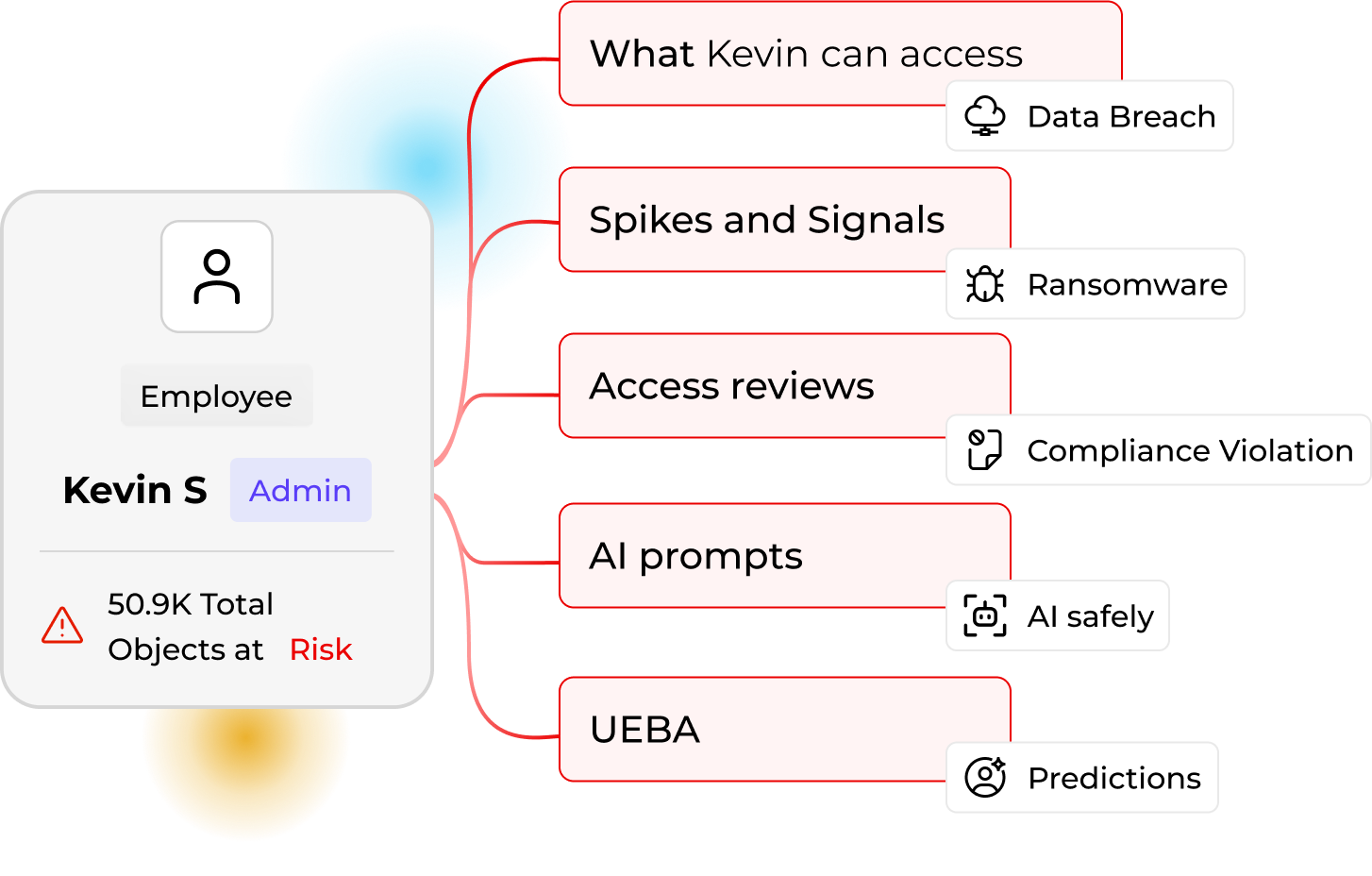
Identity-Centric Access Mapping
See exactly who is accessing data and whose data is at stake.
-
Automated Access Reviews
Launch drive, folder, group, or user reviews and remediate in one screen.
-
UEBA & Ransomware Defense
Detect abnormal behavior, suspend sessions, revoke risky access, and quarantine files.
-
Copilot & AI Governance
Inspect prompts and files to prevent data leaking through AI agents.
Traditional Industry Approach
-
Permission Lists Without Context
Static lists lack identity and data subject context, increasing risk.
-
Spreadsheet-Based Reviews
Manual exports and tickets slow down decisions and leave access open.
-
Alerts Without Remediation
Legacy tools notify but don’t act, forcing teams to triage manually.
-
Blind to AI Oversharing
Sensitive data flows uncontrolled to AI agents, circumventing access.
Identity-centric governance with automated risk reduction
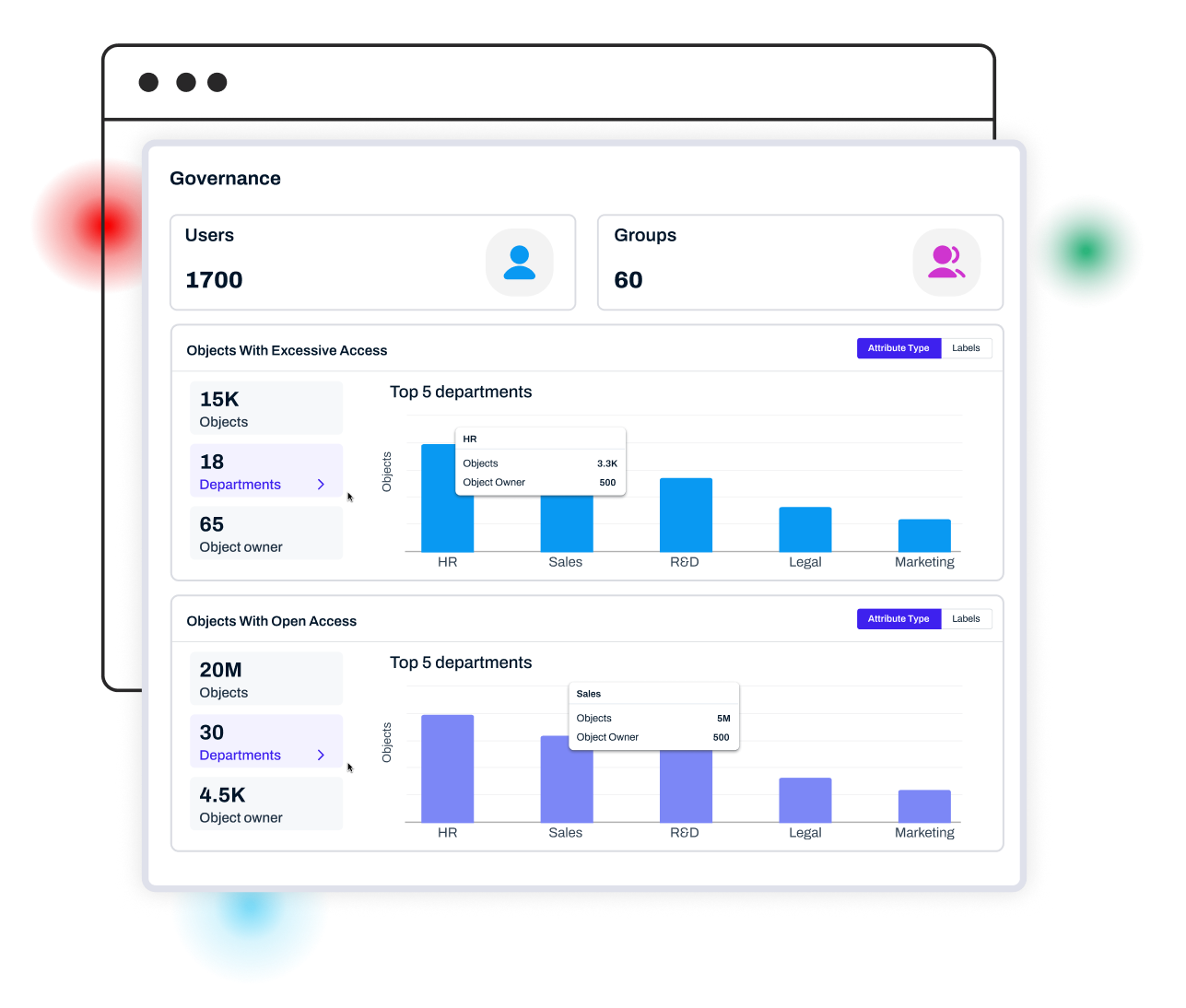
See who can access what, and whose data is at stake, then investigate, review, and remediate in one console with policy‑driven automation.
Lightbeam maps entitlements to real people through the Data Identity Graph, so you can answer exactly who can open sensitive files and why. Govern across SharePoint, Google Drive, SMB, and Copilot. Track open and excessive access, auto-revoke on policy violations, and generate immutable logs. Launch access reviews by drive, folder, group, or user, remediate in one screen, and modernize legacy shares—all from one platform.
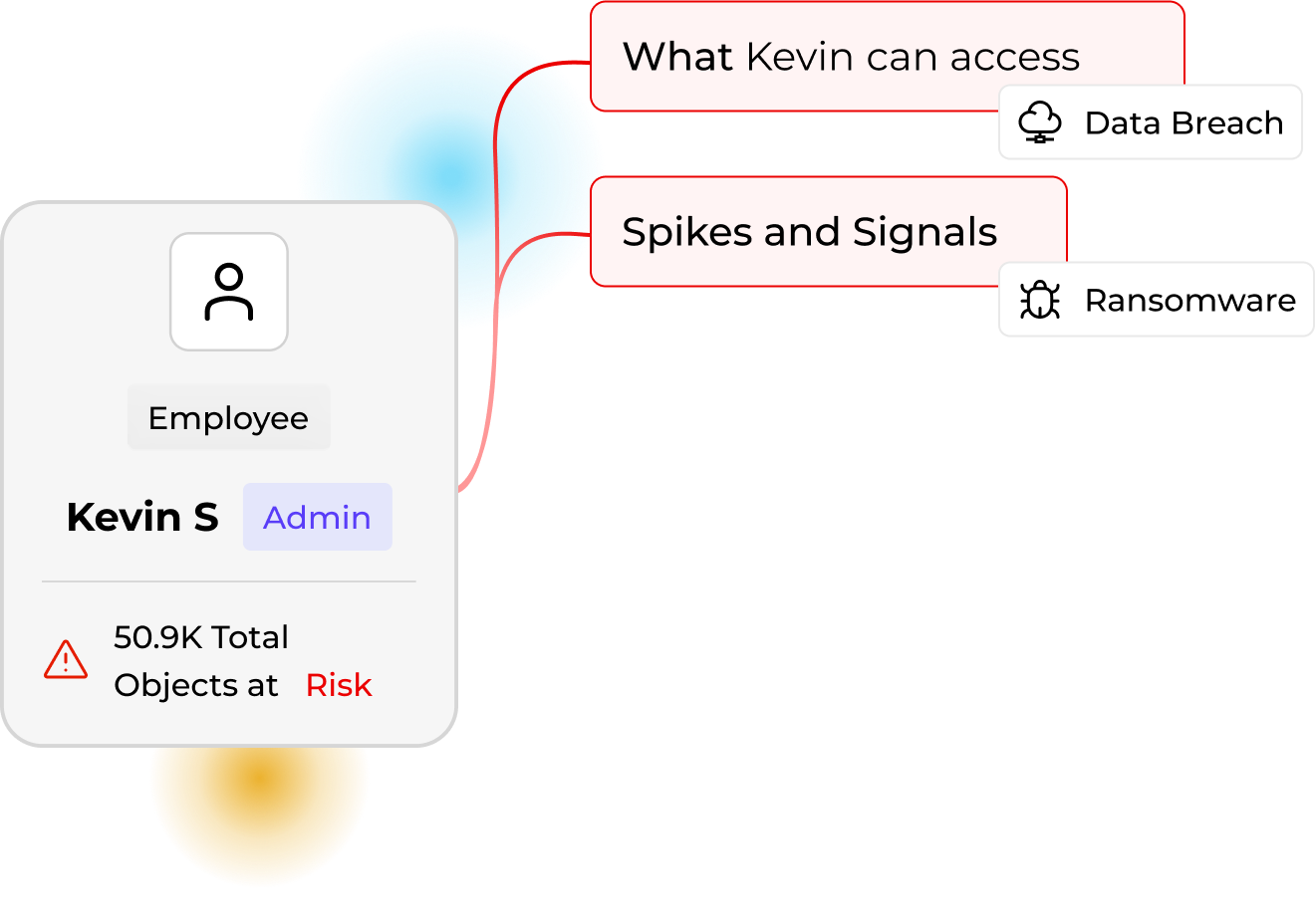
From anomaly to action: connect UEBA and ransomware signals to automated playbooks so sessions suspend and access revokes the moment risk spikes.
When behavior spikes (mass writes, encryption bursts, or anomalous file access) Lightbeam enriches the event with identity and risk context. Govern Microsoft Copilot prompts, responses, and shared files in the same way, correlating AI usage with entitlements to curb oversharing. UEBA and ransomware signals flow into governance playbooks, ensuring threats are stopped in seconds.

Prove least privilege, reduce exposure, and make audits move at speed
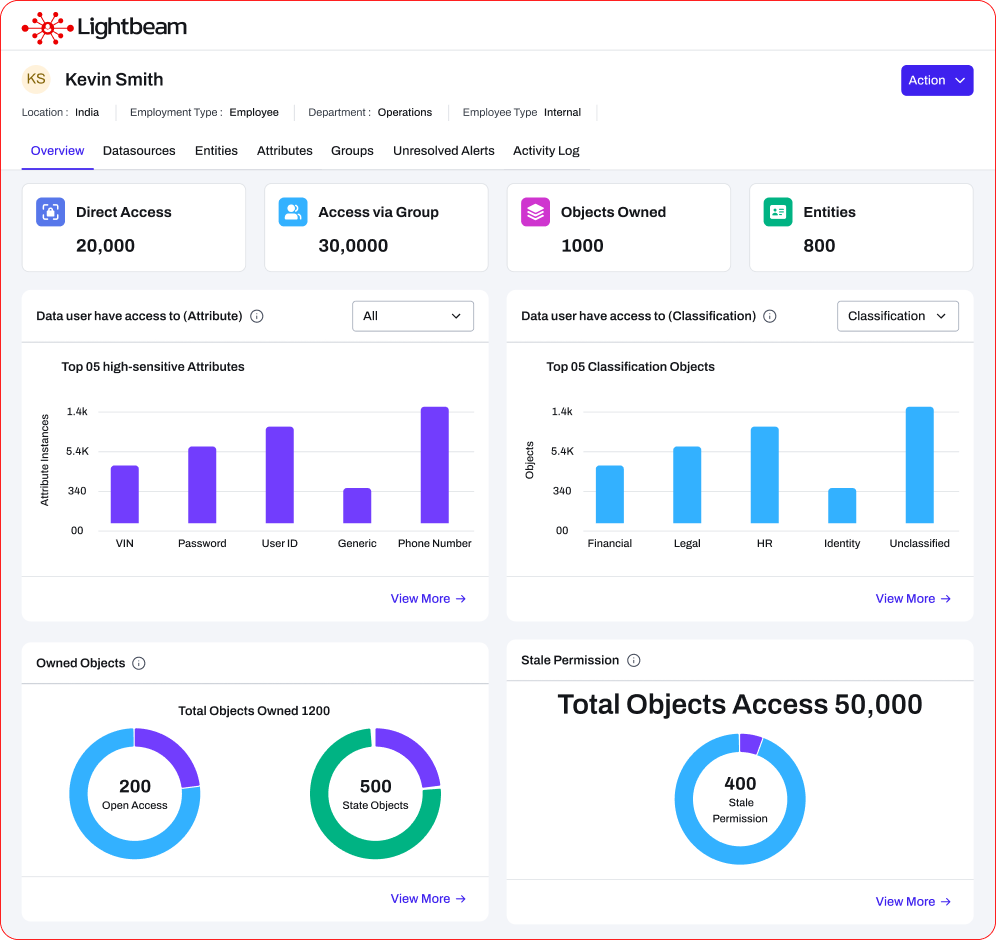
Know who can access what
Resolve every user, group, and path to a person and the data they can reach. Answer who can open sensitive files, and why, in a click to prioritize fixes.
Stop ransomware spread
Detects encryption spikes and Ransomware signals and auto-contains the blast radius in seconds.
Audit-ready access reviews
Launch access reviews by drive, folder, group, or user. Certify or revoke in one screen, then export immutable logs and CSV evidence aligned to SOC 2 and ISO 27001.
Govern AI safely
Capture AI prompts, responses, and shared files, tag sensitivity, and tie to entitlements so you can investigate and remediate sensitive data risk instantly.
Spot insider threats
UEBA flags abnormal insider activity, ransomware, and account takeovers to drive fast, policy-driven remediation.

What customers say about access governance
FAQs
Frequently Asked Questions
How is Lightbeam different from traditional access reviews or IAM tools, and what does it automate end‑to‑end for least privilege?
Traditional tools list permissions without identity or sensitivity context, forcing manual correlation and tickets. Lightbeam maps rights to real people and whose data is at stake, launches drive/folder/group/user reviews, and auto‑revokes open or excessive access with audit‑ready logs, sustaining least privilege in one console.
See Access GovernanceCan Lightbeam govern access when files aren’t flagged as sensitive, and how do file‑type and SMB policies help?
Yes. Access governance spans every file, revealing open or excessive patterns other tools miss. Enforce policies by file type to keep risky formats in check, and apply folder‑level controls on SMB shares to modernize legacy systems, all with centralized logs and playbooks.
Explore Data ClassificationHow does Access Governance integrate with Copilot, UEBA, and ransomware protection to go from signal to fix fast?
Copilot prompts, responses, and shared files are captured, classified, and tied to entitlements for safe AI use. UEBA flags anomalous access; ransomware detection spots mass encryption; both feed policy playbooks that suspend sessions or revoke access in seconds, with one audit trail from alert to action.
Explore UEBABrowse Key Resources

Blog
Summer Release 2025: Stop Ransomware Faster, Spot Insider Risk Sooner, and Prove Access is Correct
News
LightBeam Brings its AI Security and Governance Capabilities to Microsoft Copilot
As Microsoft Copilot continues to gain millions of customers worldwide, AI security and governance vendor...